HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 233
Configuring TCP attack protection, Overview, Enabling the SYN Cookie feature
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 233 highlights
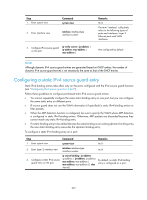
Configuring TCP attack protection Overview An attacker can attack the switch during the process of establishing a TCP connection. To prevent such an attack, the switch provides the SYN Cookie feature. Enabling the SYN Cookie feature As a general rule, the establishment of a TCP connection involves the following three handshakes. 1. The request originator sends a SYN message to the target server. 2. After receiving the SYN message, the target server establishes a TCP connection in the SYN_RECEIVED state, returns a SYN ACK message to the originator, and waits for a response. 3. After receiving the SYN ACK message, the originator returns an ACK message, establishing the TCP connection. Attackers may mount SYN Flood attacks during TCP connection establishment. They send a large number of SYN messages to the server to establish TCP connections, but they never make any response to SYN ACK messages. As a result, a large number of incomplete TCP connections are established, resulting in heavy resource consumption and making the server unable to handle services normally. The SYN Cookie feature can prevent SYN Flood attacks. After receiving a TCP connection request, the server directly returns a SYN ACK message, instead of establishing an incomplete TCP connection. Only after receiving an ACK message from the client can the server establish a connection, and then enter the ESTABLISHED state. In this way, incomplete TCP connections could be avoided to protect the server against SYN Flood attacks. Follow these guidelines when you enable the SYN Cookie feature: • If you enable MD5 authentication for TCP connections, the SYN Cookie configuration is ineffective. Then, if you disable MD5 authentication for TCP connections, the SYN Cookie configuration automatically becomes effective. For more information about MD5 authentication, see Layer 3-IP Routing Configuration Guide. • With the SYN Cookie feature enabled, only the maximum segment size (MSS), is negotiated during TCP connection establishment, instead of the window's zoom factor and timestamp. To enable the SYN Cookie feature: Step 1. Enter system view. 2. Enable the SYN Cookie feature. Command system-view tcp syn-cookie enable Remarks N/A Enabled by default Displaying and maintaining TCP attack protection 223