HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 157
Managing public keys, Overview, Configuration task list
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 157 highlights
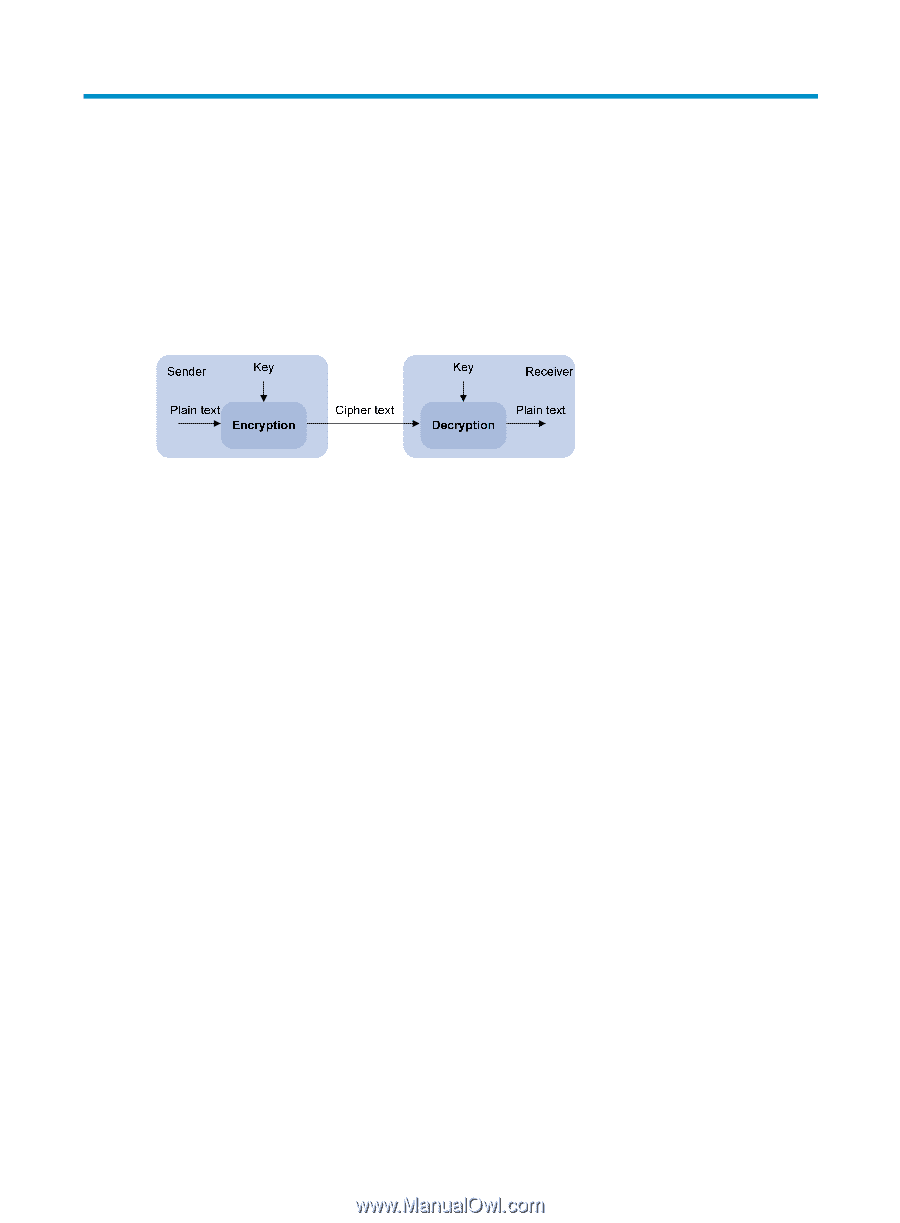
Managing public keys Overview To protect data confidentiality during transmission, the data sender uses an algorithm and a key (a character string) to encrypt the plain text data before sending the data out, and the receiver uses the same algorithm with the help of a key to decrypt the data, as shown in Figure 42. Figure 42 Encryption and decryption The keys that participate in the conversion between the plain text and the cipher text can be the same or different, dividing the encryption and decryption algorithms into the following types: • Symmetric key algorithm-The keys for encryption and decryption are the same. • Asymmetric key algorithm-The keys for encryption and decryption are different, one is the public key, and the other is the private key. The information encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. The private key is kept secret, and the public key may be distributed widely. The private key cannot be practically derived from the public key. Asymmetric key algorithms include the Revest-Shamir-Adleman Algorithm (RSA), and the Digital Signature Algorithm (DSA). Asymmetric key algorithms can be used in two scenarios for two purposes: • To encrypt and decrypt data-The sender uses the public key of the intended receiver to encrypt the information to be sent. Only the intended receiver, the holder of the paired private key, can decrypt the information. This mechanism guarantees confidentiality. Only RSA can be used for data encryption and decryption. • To authenticate a sender-This application is called digital signature. The sender "signs" the information to be sent by encrypting the information with its own private key. A receiver decrypts the information with the sender's public key and, based on whether the information can be decrypted, determines the authenticity of the information. RSA and DSA can be used for digital signature. Asymmetric key algorithms are widely used in various applications. For example, Secure Shell (SSH), Secure Sockets Layer (SSL), and Public Key Infrastructure (PKI) use the algorithms for digital signature. For information about SSH, SSL, and PKI, see "Configuring SSH2.0," "Configuring SSL," and "Configuring PKI." Configuration task list Public key configuration tasks enable you to manage the local asymmetric key pairs, and configure the peer host public keys on the local device. By completing these tasks, the local device is ready to work with applications such as SSH and SSL to implement data encryption/decryption, or digital signature. Complete these tasks to configure public keys: 147