HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 251
Configuring ARP detection, Introduction, Configuring user validity check, Configuration guideliens
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 251 highlights
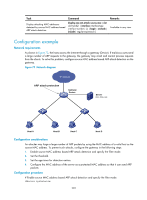
Step 2. Enable the ARP active acknowledgement function. Command Remarks arp anti-attack active-ack enable Disabled by default Configuring ARP detection Introduction ARP detection enables access devices to block ARP packets from unauthorized clients to prevent user spoofing and gateway spoofing attacks. ARP detection provides the user validity check, ARP packet validity check, and ARP restricted forwarding functions. If both ARP packet validity check and user validity check are enabled, the former one applies first, and then the latter applies. ARP detection does not check ARP packets received from ARP trusted ports. Configuring user validity check This feature enables a device to check user validity as follows: 1. Upon receiving an ARP packet from an ARP untrusted interface, the device checks the packet against the configured rules. If a match is found, the ARP packet is processed according to the matching rule. If no match is found, the device checks the packet against static IP Source Guard binding entries 2. The device compares the sender IP and MAC addresses of the ARP packet against the static IP source guard binding entries. If a match is found, the ARP packet is considered valid and is forwarded. If an entry with a matching IP address but an unmatched MAC address is found, the ARP packet is considered invalid and is discarded. If no entry with a matching IP address is found, the device compares the ARP packet's sender IP and MAC addresses against the DHCP snooping entries, 802.1X security entries, and OUI MAC addresses. 3. If a match is found from those entries, the ARP packet is considered valid and is forwarded. (For a packet to pass user validity check based on OUI MAC addresses, the sender MAC address must be an OUI MAC address and the voice VLAN must be enabled.) 4. If no match is found, the ARP packet is considered invalid and is discarded. For more information about voice VLANs and OUI MAC addresses, see Layer 2-LAN Switching Configuration Guide. Configuration guideliens Follow these guidelines when you configure user validity check: • Static IP source guard binding entries are created by using the ip source binding command. For more information, see "Configuring IP source guard." • Dynamic DHCP snooping entries are automatically generated by DHCP snooping. For more information, see Layer 3-IP Services Configuration Guide. • 802.1X security entries are generated by 802.1X. After a client passes 802.1X authentication and uploads its IP address to an ARP detection enabled device, the device automatically generates an 802.1X security entry. Therefore, the 802.1X client must be able to upload its IP address to the device. For more information, see "Configuring 802.1X." 241