HP 6125G HP 6125G & 6125G/XG Blade Switches Security Configuration Gui - Page 235
Configuring IP source guard, Overview, Static IP source guard entries, Dynamic IP source guard
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 235 highlights
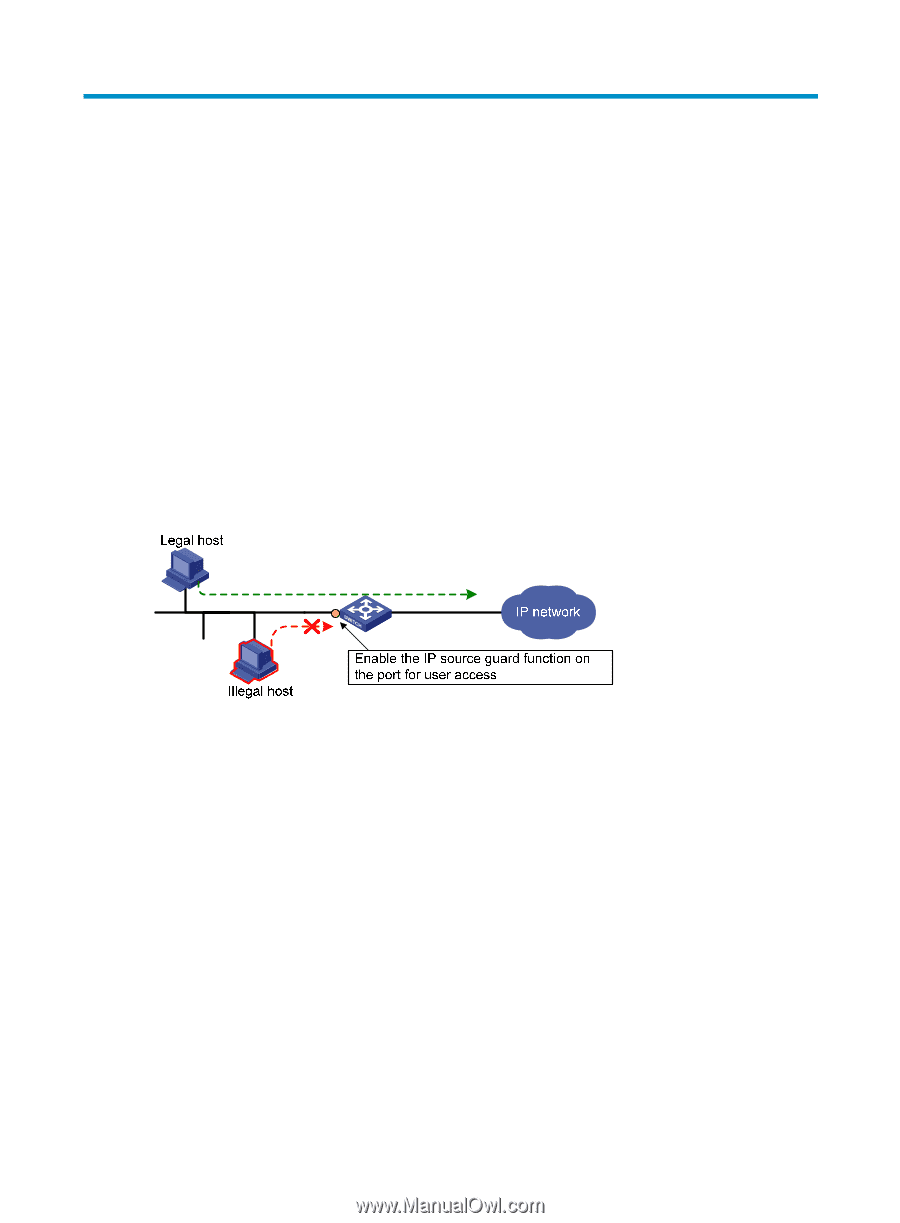
Configuring IP source guard Overview IP source guard is intended to improve port security by blocking illegal packets. For example, it can prevent illegal hosts from using a legal IP address to access the network. IP source guard can filter packets according to the packet source IP address and source MAC address. IP source guard entries fall into the following types: • IP-port binding entry • MAC-port binding entry • IP-MAC-port binding entry After receiving a packet, an IP source guard-enabled port obtains the key attributes (source IP address and source MAC address) of the packet and then looks them up in the IP source guard entries. If there is a match, the port forwards the packet. Otherwise, the port discards the packet, as shown in Figure 68. Figure 68 Diagram for the IP source guard function A binding entry can be statically configured or dynamically added. Static IP source guard entries A static IP source guard entry is configured manually. A port forwards a packet only when the source IP address and source MAC address of the packet exactly match an IP source guard entry on the port. IP source guard entries are suited to check the validity of access users, especially in LAN that has only a few hosts and the hosts use statically configured IP addresses. For example, you can configure an IP source guard entry on a port connecting a server, permitting only the packets exchanged with the server to pass the port. A static IPv4 source guard entry filters IPv4 packets received by the port or cooperates with ARP detection to check the validity of users. For information about ARP detection, see "Configuring ARP attack protection. Dynamic IP source guard entries Dynamic IP source guard entries are generated dynamically according to client entries on the DHCP snooping or DHCP relay agent device. They are suitable for scenarios where many hosts reside on a LAN 225