Dell EqualLogic PS6210XS EqualLogic Group Manager Administrator s Guide PS Ser - Page 65
Differences Between Authentication Methods, Administration Account Attributes
 |
View all Dell EqualLogic PS6210XS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 65 highlights
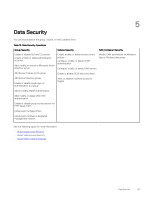
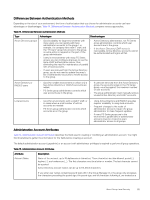
Differences Between Authentication Methods Depending on the size of your environment, the form of authorization that you choose for administrator accounts can have advantages or disadvantages. Table 14. Differences Between Authentication Methods compares various approaches. Table 14. Differences Between Authentication Methods Type Advantages Disadvantages Active Directory groups • Good scalability for large environments with many users; you can quickly add many administrator accounts to the group. For example, if a company hires new IT staff, and the "IT Users" group has access to the group, no extra action is required on the part of the group administrator. • Active Directory administrator, not PS Series group administrator, controls which user accounts are in the group. • If the Active Directory/LDAP server is inaccessible, Active Directory accounts cannot be authenticated and logins will fail. • Useful in environments with many PS Series groups; you can configure all groups to use the same LDAP authentication server, thus eliminating the need for maintenance of parallel sets of local accounts. • If users are removed from the Active Directory group, you do not need to update the array's list of administrator accounts to revoke access to the group. Active Directory or RADIUS users • Good for smaller environments in which only a • If users are removed from the Active Directory few Active Directory or RADIUS accounts are group, the accounts remain in the PS Series added. group, counting against the maximum number • PS Series group administrator controls which of user accounts. user accounts are in the group. • The group administrator must manually remove unused Active Directory and LDAP accounts. Local accounts • Good for environments with a small IT staff, or • Using Active Directory and RADIUS provides in cases where a small number of ad-hoc superior scalability to using local accounts. accounts are needed. • Frequent changes to the roster of • PS Series group administrator controls which administrator accounts require the group accounts are in the group. administrator to make frequent updates. • If many PS Series groups are in the environment, parallel sets of administrator accounts must be created to grant administrator access to all groups. Administration Account Attributes Table 15. Administration Account Attributes describes the fields used in creating or modifying an administration account. You might find it beneficial to gather the information for the fields before creating an account. The default administration account (grpadmin) or an account with administrator privileges is required to perform all group operations. Table 15. Administration Account Attributes Attribute Account Name Description Name of the account, up to 16 alphanumeric characters. These characters are also allowed: period (.), hyphen (-), and underscore (_). The first character must be a letter or number. The last character cannot be a period. Active Directory account names can be up to 511 ASCII characters. If you enter user names containing pound signs (#) in the Group Manager CLI, the group only processes the characters preceding the pound sign; the pound sign, and all characters following it, are treated as a About Group-Level Security 65