Dell EqualLogic PS6210XS EqualLogic Group Manager Administrator s Guide PS Ser - Page 66
About Security Access Protocols, SSH Key Pair Authentication, Contact Information
 |
View all Dell EqualLogic PS6210XS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 66 highlights
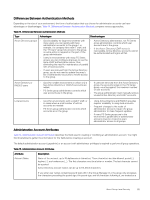
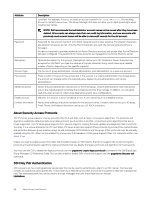
Attribute Password Description comment. For example, if you try to create an account named AdminUser#Account, the resulting account is named AdminUser. The Group Manager GUI does not allow you to input pound signs when creating user names. NOTE: Dell recommends that administrator account names not be reused after they have been deleted. All accounts can always view their own audit log information, and new accounts with previously used account names will be able to view audit records for the old account. Password for the account can be 3 to 13 ASCII characters and is case-sensitive. Punctuation characters are allowed, but spaces are not. Only the first 8 characters are used; the rest are ignored (without a message). You are not required to provide passwords for Active Directory accounts and groups after Active Directory has been configured. The passwords for these accounts are managed by the Active Directory server. Description Account type Pool access Additional access Enable account Contact Information Optional description for the account. Descriptions can be up to 127 characters. Fewer characters are accepted for this field if you type the value as a Unicode character string, which takes up a variable number of bytes, depending on the specific character. Can be one of group administrator, volume administrator, pool administrator, or a read-only account. Pools to which the account has access and, if the account is a volume administrator, the storage quota the account can manage within the selected pools. Applies to pool administrators and volume administrators. Grants the pool administrator read access to the entire group. Volume administrators have read access only to the individual pools containing the storage quotas that they manage. In addition, you can grant read-only users access to collect array diagnostics and/or save configurations. Whether the account is active (enabled) or not. A user cannot log in to a disabled account. Name, email address, and phone numbers for the account owner. Contact name can be up to 63 bytes. Email, Phone, and Mobile information can be up to 31 ASCII characters. About Security Access Protocols The PS Series group supports security protocols SSL/TLS and SSH, with a range of encryption algorithms. The protocols and algorithms enabled by default include some older protocols (such as SSH v1 and SSL v2) and encryption algorithms that are no longer supported. The PS Series group supports SCP (secure copy) for copying firmware updates and diagnostic files to and from the array. It is a secure alternative to FTP and Telnet. PS Series arrays also support IPSec protocols to provide IPSec authentication and protection between group member arrays as well as between iSCSI initiators and the group. IPSec protocols must be manually enabled using the CLI. IPSec can be enabled for a group only if all members of that group support IPSec. For more information, see About IPsec. Unless you need to enable access from older clients (web browsers or SSH clients) that do not support the current encryption protocols and authentication algorithms, Dell recommends that you disable the legacy protocols and algorithms for best security. You must use the CLI to disable the legacy protocols; see the grpparams crypto-legacy-protocols command in the Dell EqualLogic Group Manager CLI Reference Guide. You can also enable or disable SSH v1 protocol support; see the grpparams cliaccess-ssh command. SSH Key Pair Authentication SSH key pairs are two cryptographically secure keys that can be used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key. The private key is retained by the client and can be encrypted on disk with a passphrase only. The associated public key can be used to encrypt messages that only the private key can decrypt. Limitations 66 About Group-Level Security