Linksys WIP310 SPA500 Series and WIP310 IP Phone Administration Guide - Page 127
Factors Affecting Voice Quality, Configuring Security, Quality, and Network Features, Codec, Bandwidth
 |
UPC - 745883580927
View all Linksys WIP310 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 127 highlights
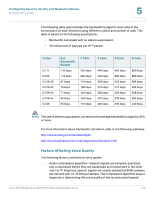
Configuring Security, Quality, and Network Features Ensuring Voice Quality 5 The following table approximates the bandwidth budget for each side of the conversation (in each direction) using different codecs and number of calls. This table is based on the following assumptions: • Bandwidth calculated with no silence suppression • 20 millisecond of payload per RTP packet Codec G.711 G.722 G.726-40 G.726-32 G.726-24 G.726-16 G.729 Est. Bandwidth Budget 110 kbps 110 kbps 87 kbps 79 kbps 71 kbps 63 kbps 55 kbps 2 Calls 220 kbps 220 kbps 174 kbps 158 kbps 142 kbps 126 kbps 110 kbps 4 Calls 440 kbps 440 kbps 348 kbps 316 kbps 284 kbps 252 kbps 220 kbps 6 Calls 660 kbps 660 kbps 522 kbps 474 kbps 426 kbps 378 kbps 330 kbps 8 Calls 880 kbps 880 kbps 696 kbps 632 kbps 568 kbps 504 kbps 440 kbps NOTE The use of silence suppression can reduce the average bandwidth budget by 30% or more. For more information about bandwidth calculation, refer to the following websites: http://www.erlang.com/calculator/lipb/ http://www.packetizer.com/voip/diagnostics/bandcalc.html Factors Affecting Voice Quality The following factors contribute to voice quality: • Audio compression algorithm-Speech signals are sampled, quantized, and compressed before they are packetized and transmitted to the other end. For IP Telephony, speech signals are usually sampled at 8000 samples per second with 12-16 bits per sample. The compression algorithm plays a large role in determining the voice quality of the reconstructed speech Cisco SPA 500 Series and WIP310 IP Phone Administration Guide 116