D-Link DGS-1510-28P User Manual - Page 328
Security > BPDU Attack Protection, BPDU Attack Protection State, State, From Port / To Port, Block
 |
View all D-Link DGS-1510-28P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 328 highlights
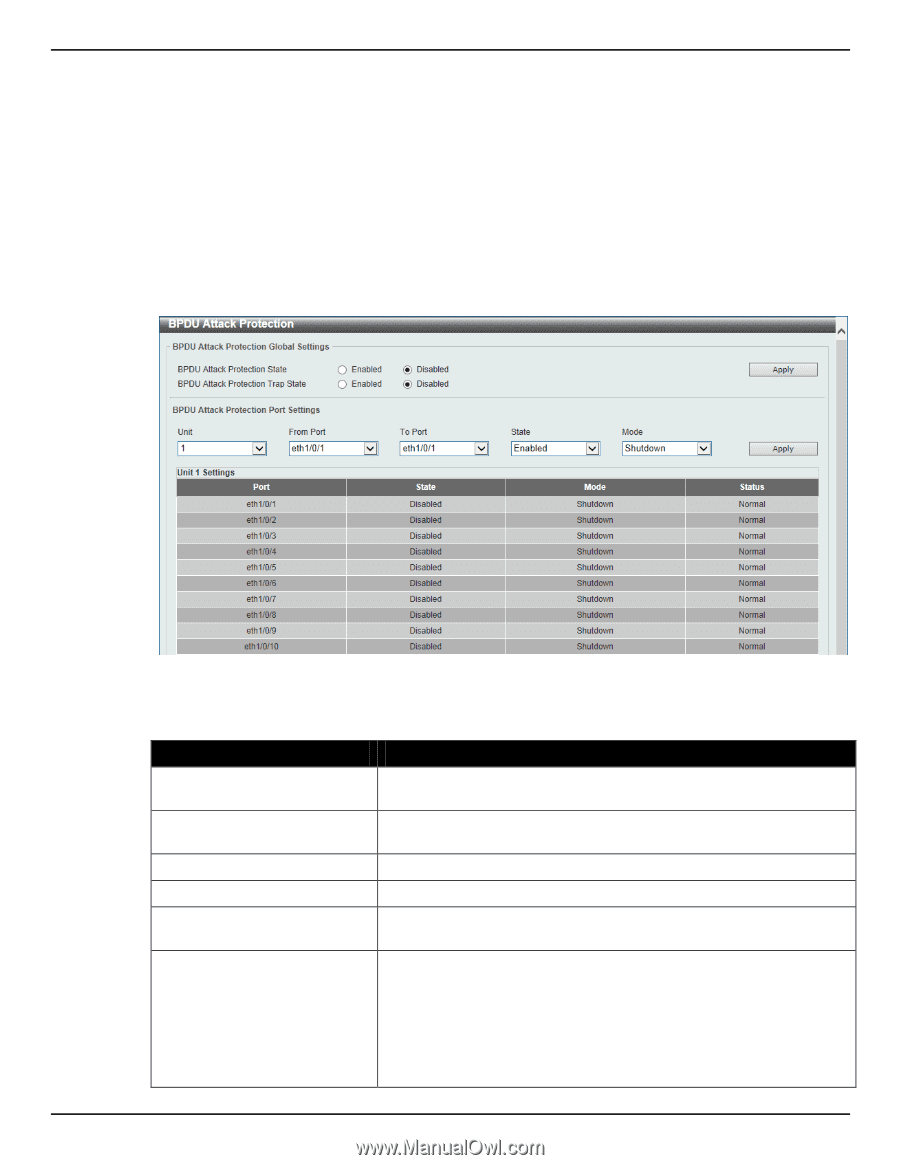
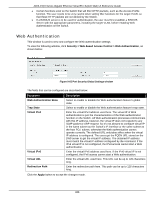
DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide The under attack state have three modes: drop, block, and shutdown. A BPDU protection enabled port will enter an under attack state when it receives one STP BPDU packet and it will take action based on the configuration. Thus, BPDU protection can only be enabled on the STP-disabled port. BPDU protection has a higher priority than the FBPDU setting configured by configure STP command in the determination of BPDU handling. That is, when FBPDU is configured to forward STP BPDU but BPDU protection is enabled, then the port will not forward STP BPDU. BPDU protection also has a higher priority than the BPDU tunnel port setting in determination of BPDU handling. That is, when a port is configured as BPDU tunnel port for STP, it will forward STP BPDU. But if the port is BPDU protection enabled. Then the port will not forward STP BPDU. To view the following window, click Security > BPDU Attack Protection, as shown below: Figure 9-62 BPDU Attack Protection window The fields that can be configured are described below: Parameter BPDU Attack Protection State BPDU Attack Protection Trap State Unit From Port / To Port State Mode Description Select to enable or disable the BPDU attack protection feature's global state here. Select to enable or disable the BPDU attack protection feature's trap state here. Select the switch unit that will be used for this configuration here. Select the appropriate port range used for the configuration here. Select to enable or disable the BPDU attack protection feature's state on the port(s) specified. Select the BPDU attack protection feature's mode that will be applied to the port(s) specified. Options to choose from are Drop, Block and Shutdown. Drop - Drop all received BPDU packets when the port enters under attack state. Block - Drop all packets (include BPDU and normal packets) when the port enters under attack state. 320