Dell PowerConnect W-IAP92 Dell Instant 6.1.2.3-2.0.0.0 User Guide - Page 49
Access, Allow any to all destinations, Edit Rule box, New Rule, Finish, Networks
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 49 highlights
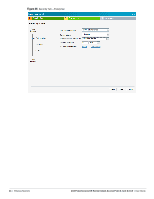
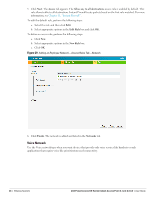
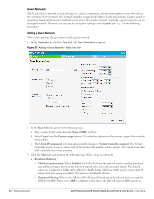
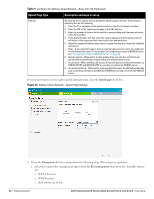
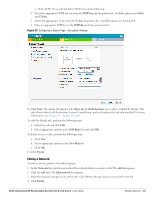
Table 8 Conditions for Adding a Voice Network-Security Tab (Continued) If then, You want to use the default security level, Personal, You select the Open security level Perform the following steps: 1. Select the required key options from the Key management drop-down list. Available options are: WPA-2 Personal WPA Personal Both (WPA-2 & WPA) Static WEP If you selected Static WEP, then do the following: Select appropriate WEP key size from the WEP key size drop-down list. Available options are 64-bit and 128-bit. Select appropriate Tx key from the Tx Key drop-down list. Available options are 1, 2, 3, and 4. Enter an appropriate WEP key in the WEP Key text box and reconfirm. For more information on encryption and recommended encryption type, see Chapter 9, "Encryption" . 2. Enter a passphrase in the Passphrase text box and reconfirm. 3. Select the required option from the Mac authentication drop-down list. Available options are: None-This option provides open authentication. Any client that requests association is allowed to connect to the network. Open authentication is not recommended unless you want users to gain quick access to the network. External RADIUS Server-For information on configuring an external RADIUS server, see "Configuring an External RADIUS Server" on page 79. Select the required Mac authentication from the Mac authentication drop-down list. Available options are: None-This option provides open authentication. Any client that requests association is allowed to connect to the network. Open authentication is not recommended unless you want users to gain quick access to the network. External RADIUS Server-For information on configuring an external RADIUS server, see "Configuring an External RADIUS Server" on page 79. 4. Click Next. The Access tab appears. The Allow any to all destinations access rule is enabled by default. This rule allows traffic to all destinations. Instant Firewall treats packets based on the first rule matched. For more information, see Chapter 11, "Instant Firewall" . To edit the default rule, perform the following steps: a. Select the rule and click Edit. b. Select appropriate options in the Edit Rule box and click OK. To define an access rule, perform the following steps: a. Click New. b. Select appropriate options in the New Rule box. c. Click OK. 5. Click Finish. The network is added and listed in the Networks tab. Dell PowerConnect W-Series Instant Access Point 6.1.2.3-2.0.0.0 | User Guide Wireless Network | 49