Dell PowerConnect W-IAP92 Dell Instant 6.1.3.1-3.0.0.0 User Guide - Page 109
MAC Authentication, Configuring MAC Authentication, NAS IP address
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 109 highlights
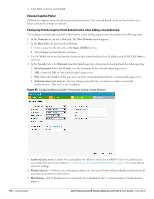
MAC Authentication Media Access Control (MAC) authentication is used to authenticate devices based on their physical MAC addresses. It is an early form of filtering. MAC authentication requires that the MAC address of a machine must match a manually defined list of addresses. This form of authentication does not scale past a handful of devices, because it is difficult to maintain the list of MAC addresses. Additionally, it is easy to change the MAC address of a station to match one on the accepted list. This spoofing is trivial to perform with built-in driver tools, and it should not be relied upon to provide security. MAC authentication can be used alone, but typically it is combined with other forms of authentication, such as WEP authentication. Because MAC addresses are easily observed during transmission and easily changed on the client, this form of authentication should be considered nothing more than a minor hurdle that will not deter the determined intruder. It is recommended against the use of MAC based authentication. Configuring MAC Authentication To enable MAC Authentication for a wireless network, perform the following steps: 1. In the Network tab, click the network for which you want to enable MAC authentication. The edit link for the network appears. 2. Click the edit link and navigate to the Security tab. 3. For a network with Personal or Open security level, select Enabled from the MAC Authentication drop-down list. 4. Select New from the Authentication server 1 drop-down list perform the following steps: a. Name: Enter the name of the new external RADIUS server. b. IP address: Enter the IP address of the external RADIUS server. c. Auth port: Enter the authorization port number of the external RADIUS server. The port number is set to 1812 by default. d. Accounting port: Enter the accounting port number. This port is used to send accounting records to the RADIUS server. The port number is set to 1813 by default e. Shared key: Enter a shared key for communicating with the external RADIUS server. f. Timeout: Specify a number between1 and 30 seconds. User will be disconnected after this time. The default value is 5 seconds. g. Retry count: Specify a number between 1 and 5. Indicates the maximum number of authentication requests that are sent to server group, and the default value is 3 requests. h. RFC 3576: When enabled, the Access Points will process RFC 3576-compliant Change of Authorization (CoA) and Disconnect messages from the RADIUS server. Disconnect messages cause a user session to be terminated immediately, whereas CoA messages modify session authorization attributes such as data filters. i. NAS IP address: Enter the Virtual Controller IP address. The NAS IP address is the Virtual Controller IP address that is sent in data packets. j. NAS identifier: Use this to configure strings for RADIUS attribute 32, NAS Identifier, to be sent with RADIUS requests to the RADIUS server. 5. Click OK to continue. Dell PowerConnect W-Series Instant Access Point 6.1.3.1-3.0.0.0 | User Guide Authentication | 109