Dell PowerConnect W-IAP92 Dell Instant 6.1.3.1-3.0.0.0 User Guide - Page 120
Creating Role Assignment Rules,
 |
View all Dell PowerConnect W-IAP92 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 120 highlights
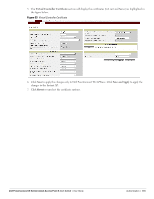
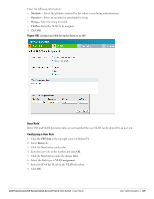
Figure 95 Creating a New User Role 8. Click OK. The Allow any to all destinations access rule is enabled by default. This rule allows traffic to all destinations. To create new access rules, see "Examples for Access Rules" on page 131. 9. To delete a user role, select the user role and click the Delete button. 10. Assign pre-authentication role- Use this option if you want to allow some access to users even before they are authenticated. 11. Enforce Machine Authentication- You can assign different rights to clients based on whether their hardware device supports machine authentication. Machine Auth is only supported for Windows devices, so this can be used to distinguish between Windows devices and other devices such as ipads. Machine Auth only role - This is the case of a Windows machine with no user logged in. The device supports machine authentication and has a valid RADIUS account, but a user has not yet logged in and authenticated. User Auth only role - This is the case of a known user or a non-Windows device. The device does not support machine auth or does not have a RADIUS account, but the user is logged in and authenticates. When a device does both Machine and User authentication, the user will get the default role or the derived role based on the RADIUS attribute. To configure Machine Authentication, do the following: 1. In the Roles window, create a role for Machine auth only and User auth only. 2. Configure Access Rules for these roles by selecting the role, and applying the rule. Refer to "Examples for Access Rules" on page 131 for procedures to create access rules. 3. Select Enforce Machine Authentication and specify these two roles. 4. Click Finish to apply these changes. Creating Role Assignment Rules This section has the rules for determining which role will be assigned for each authenticated client. NOTE: When Enforce Machine Authentication is enabled, both the device and the user must be authenticated for the role assignment rule to apply. To create role assignment rules for the user role, perform the following steps: 1. Click New in the Role Assignment Rules section of the window. The default user role is the newly created user role. 120 | Role Derivation Dell PowerConnect W-Series Instant Access Point 6.1.3.1-3.0.0.0 | User Guide