HP StorageWorks MSA 2/8 HP StorageWorks Secure Fabric OS V1.0 User Guide (AA-R - Page 59
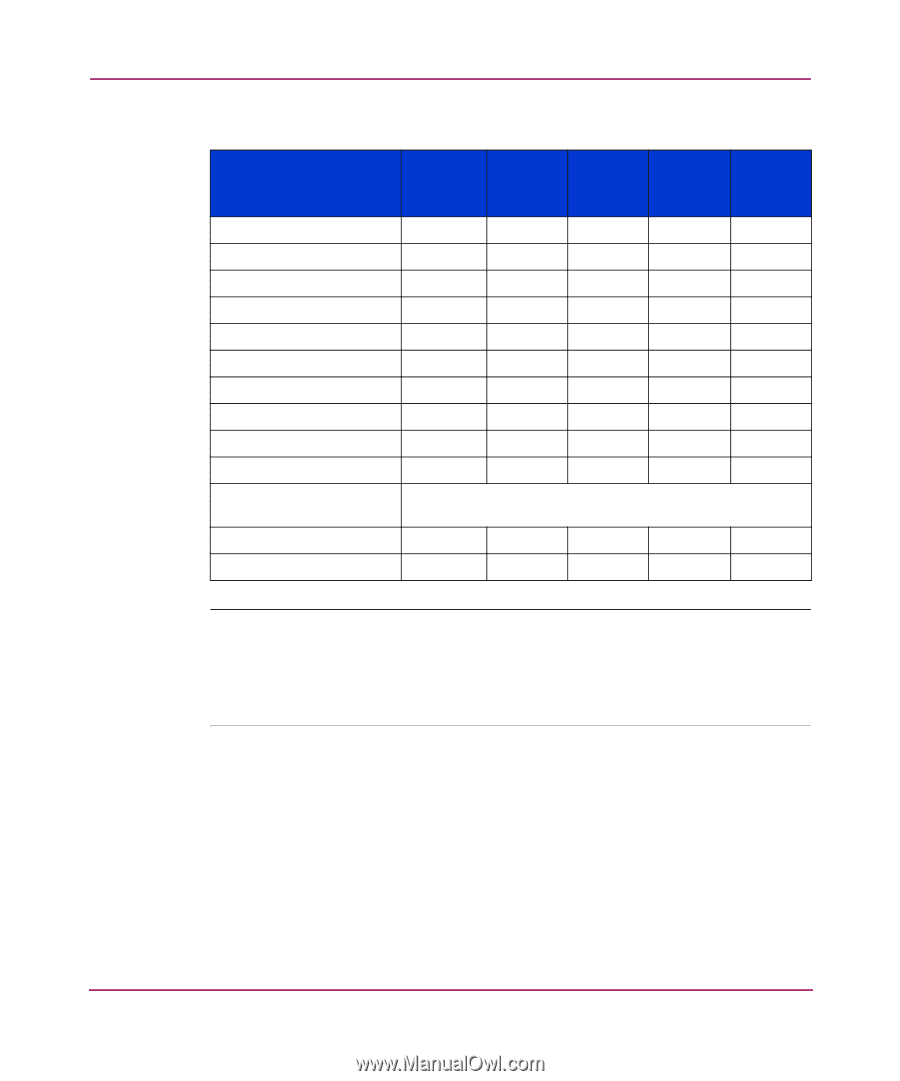
Table 3: Valid Methods for Specifying Policy Members, Creating a MAC Policy
 |
View all HP StorageWorks MSA 2/8 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 59 highlights
Creating Secure Fabric OS Policies Table 3: Valid Methods for Specifying Policy Members Policy Name FCS_POLICY MAC Policies RSNMP_POLICY WSNMP_POLICY TELNET_POLICY HTTP_POLICY API_POLICY MS_POLICY SERIAL_POLICY FRONTPANEL_POLICY OPTIONS_POLICY DCC_POLICY_nnn SCC_POLICY IP Address Device Port WWN Switch Domain Switch WWN IDs Names No No Yes Yes Yes No No No No No Yes No No No No Yes No No No No Yes No No No No Yes No No No No Yes No No No No No Yes No No No No No Yes Yes Yes No No Yes Yes Yes For information about valid input, see "Creating an Options Policy" on page 70. No Yes Yes Yes Yes No No Yes Yes Yes Note: If IP addresses are used, you can use "0" in an octet to indicate that any number can be matched for that octet. For example, 192.168.11.0 would allow access for all IP devices in the network 192.168.11. If Domain IDs or switch names are used, the corresponding switches must be in the fabric for the command to succeed. Creating a MAC Policy You can create MAC policies to restrict the following management access to the fabric: ■ Access by hosts using SNMP, telnet/sectelnet/SSH, HTTP, or API ■ Access by device ports using Management Server ■ Access through switch serial ports and front panels Secure Fabric OS Version 1.0 User Guide 59