HP StorageWorks MSA 2/8 HP StorageWorks Secure Fabric OS V1.0 User Guide (AA-R - Page 62
Telnet Policy, are in a physically secure area.
 |
View all HP StorageWorks MSA 2/8 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 62 highlights
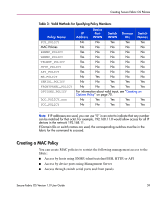
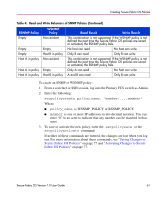
Creating Secure Fabric OS Policies Example: Creating a WSNMP and an RSNMP policy to allow only IP addresses that match 192.168.5.0 read and write access to the fabric: primaryfcs:admin> secPolicyCreate "WSNMP_POLICY", "192.168.5.0" WSNMP_POLICY has been created. primaryfcs:admin> primaryfcs:admin> secPolicyCreate "RSNMP_POLICY", "192.168.5.0" RSNMP_POLICY has been created. primaryfcs:admin> Telnet Policy You can create the Telnet policy to specify the workstations that can use sectelnet or SSH to connect to the fabric. The policy is named TELNET _POLICY and contains a list of the IP addresses for the trusted workstations (workstations that are in a physically secure area). Note: Static host IP addresses are required to implement this policy effectively. Do not use DHCP for hosts that are in the TELNET_POLICY, because as soon as the IP addresses change, the hosts will no longer be able to access the fabric. Restricting output (such as placing a session on "hold" by use of a command or keyboard shortcut) is not recommended. This policy pertains to sectelnet, which can be utilized as soon as a digital certificate is installed on the switch, and SSH. It does not pertain to telnet access because telnet is not available in Secure Mode. Note: An empty TELNET_POLICY blocks all telnet access. To prevent this, keep one or more members in the Telnet policy. If you require an empty Telnet policy, leave a meaningful entry in the API, HTTP, or SERIAL policies to provide some form of access to the switch. If you want to restrict CLI access over the network to SSH, disable telnet as described under "Telnet" on page 15. The possible telnet policy states are shown in Table 5. 62 Secure Fabric OS Version 1.0 User Guide