HP 6125G HP 6125G & 6125G/XG Blade Switches Fundamentals Configuration - Page 74
SNMP login control configuration example, Network requirements
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
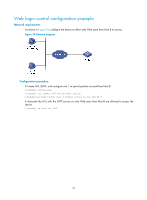
Step 5. Apply the ACL to an SNMP community, group or user. Command • SNMPv1/v2c community: snmp-agent community { read | write } community-name [ mib-view view-name ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * • SNMPv1/v2c group: snmp-agent group { v1 | v2c } group-name [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * • SNMPv3 group: snmp-agent group v3 group-name [ authentication | privacy ] [ read-view read-view ] [ write-view write-view ] [ notify-view notify-view ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * • SNMPv1/v2c user: snmp-agent usm-user { v1 | v2c } user-name group-name [ acl acl-number | acl ipv6 ipv6-acl-number ] * • SNMPv3 user: snmp-agent usm-user v3 user-name group-name [ [ cipher ] authentication-mode { md5 | sha } auth-password [ privacy-mode { 3des | aes128 | des56 } priv-password ] ] [ acl acl-number | acl ipv6 ipv6-acl-number ] * Remarks For more information about SNMP, see Network Management and Monitoring Configuration Guide. SNMP login control configuration example Network requirements As shown in Figure 33, configure the device to allow only NMS users from Host A and Host B to access. Figure 33 Network diagram 68