HP StorageWorks 8/80 Brocade Web Tools Administrator's Guide v6.2.0 (53-100119 - Page 275
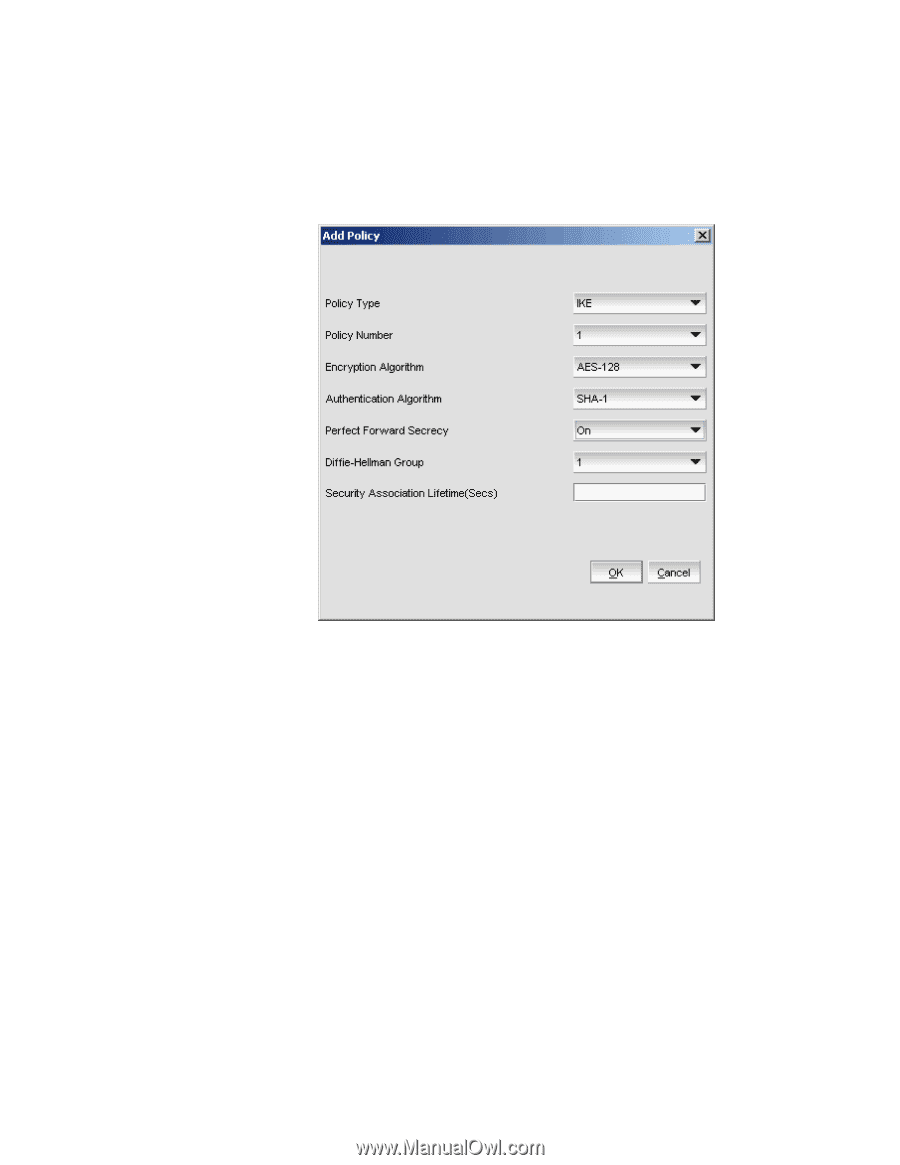
Establishing an IKE policy for an FCIP tunnel
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 275 highlights
IPSec over FCIP 17 Establishing an IKE policy for an FCIP tunnel 1. From the IKE tab of the IPSec Policies screen, select Create. An Add Policy dialog box is displayed (Figure 121). FIGURE 121 Add Policy (IKE for FCIP) 2. Policy Type provides a way to toggle between IKE and IPSec Add Policy dialog boxes. Make sure the Policy Type is set to IKE. 3. Assign a policy number. The Policy Number selector allows you to choose a number between 1 and 32. 4. Choose the Encryption Algorithm used in this policy. The choices are 3DES, AES-128, and AES_256. 5. Choose an Authentication Algorithm for this policy. The choices are SHA-1, MD5, and AESXCBC. 6. Turn Perfect Forward Secrecy on or off. The default is On. Perfect Forward Secrecy (PFS) provides additional security by means of a Diffie-Hellman shared secret value. With PFS, if one key is compromised, previous and subsequent keys are secure because they are not derived from previous keys. 7. Choose a Diffie-Hellman Group association. The choices are 1 (modp768), and 14 (modp2048). 8. Set a Security Association Lifetime (in seconds). The Security Association Lifetime is a time value in seconds. When this timer expires, the security association (SA) is rekeyed. This limits the amount of time a given key is available to a potential attacker. 9. Click OK. Web Tools Administrator's Guide 247 53-1001194-01