HP DesignJet Z2600 User guide - Page 121
Non-Secure Fast Erase, Secure Sanitizing Erase, in using Secure Disk Erase from Web JetAdmin
 |
View all HP DesignJet Z2600 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 121 highlights
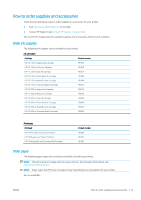
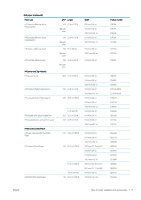
● Non-Secure Fast Erase: all pointers to the information are erased. The information itself remains on the hard disk until the disk space it occupies is needed for other purposes, and it is then overwritten. While it remains on the disk, it is difficult for most people to access, but may be accessed using software designed for the purpose. This is the normal method in which files are erased on most computer systems; it is the fastest method but the least secure. ● Secure Fast Erase: all pointers to the information are erased, and the information itself is also overwritten with a fixed character pattern. This method is slower than Non-Secure Fast Erase, but more secure. It may still be possible to access fragments of the erased information by using special tools to detect residual magnetic traces. ● Secure Sanitizing Erase: all pointers to the information are erased, and the information itself is repetitively overwritten using an algorithm designed to eliminate any residual traces. This is the slowest method, but the most secure. Secure Sanitizing Erase meets the US Department of Defense 5220-22.m requirements for clearing and sanitization of disk media. This is the default security level when using Secure Disk Erase. Secure Disk Erase is one of the facilities provided by Web JetAdmin, which is HP's free Web-based print management software: see http://www.hp.com/go/webjetadmin. If you have difficulty in using Secure Disk Erase from Web JetAdmin, contact HP Support: see Contact HP Support on page 164. NOTE: If you choose to erase the whole hard disk, you may be asked to restart the printer several times during the process, which will take about 6 hours with Secure Disk Erase or 24 hours with Secure Sanitizing Erase. ENWW Secure Disk Erase 113