Netgear FVS318G FVS318G User Manual - Page 104
Configuring XAUTH for VPN Clients, IPsec Host., IKE Policies, XAUTH, Extended Authentication
 |
UPC - 606449064827
View all Netgear FVS318G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 104 highlights
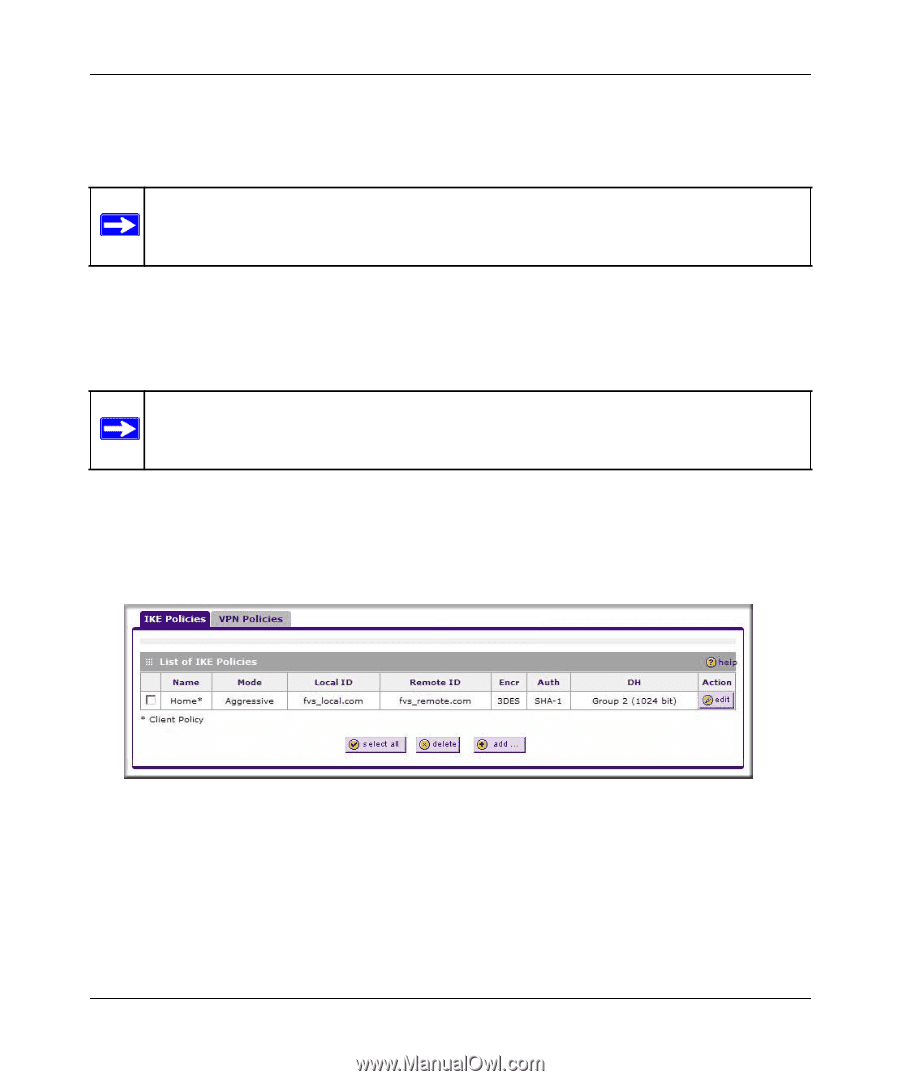
ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual • IPsec Host. If you want authentication by the remote gateway, enter a User Name and Password to be associated with this IKE policy. If this option is chosen, the remote gateway must specify the user name and password used for authenticating this gateway. Note: If a RADIUS-PAP server is enabled for authentication, XAUTH will first check the local User Database for the user credentials. If the user account is not present, the VPN firewall will then connect to a RADIUS server. Configuring XAUTH for VPN Clients Once the XAUTH has been enabled, you must establish user accounts on the User Database to be authenticated against XAUTH, or you must enable a RADIUS-CHAP or RADIUS-PAP server. Note: You cannot modify an existing IKE policy to add XAUTH while the IKE policy is in use by a VPN policy. The VPN policy must be disabled before you can modify the IKE policy. To enable and configure XAUTH: 1. Select VPN > IPsec VPN from the main menu. 2. Click the IKE Policies tab. The IKE Policies screen is displayed. Figure 5-18 3. You can add XAUTH to an existing IKE Policy by clicking Edit adjacent to the policy to be modified or you can create a new IKE Policy incorporating XAUTH by clicking Add. 4. In the Extended Authentication section, choose the Authentication Type from the pulldown menu which will be used to verify user account information. Select 5-18 Virtual Private Networking Using IPsec 1.1 November, 2009