Netgear FVS318G FVS318G User Manual - Page 123
Managing Certificates - issues
 |
UPC - 606449064827
View all Netgear FVS318G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 123 highlights
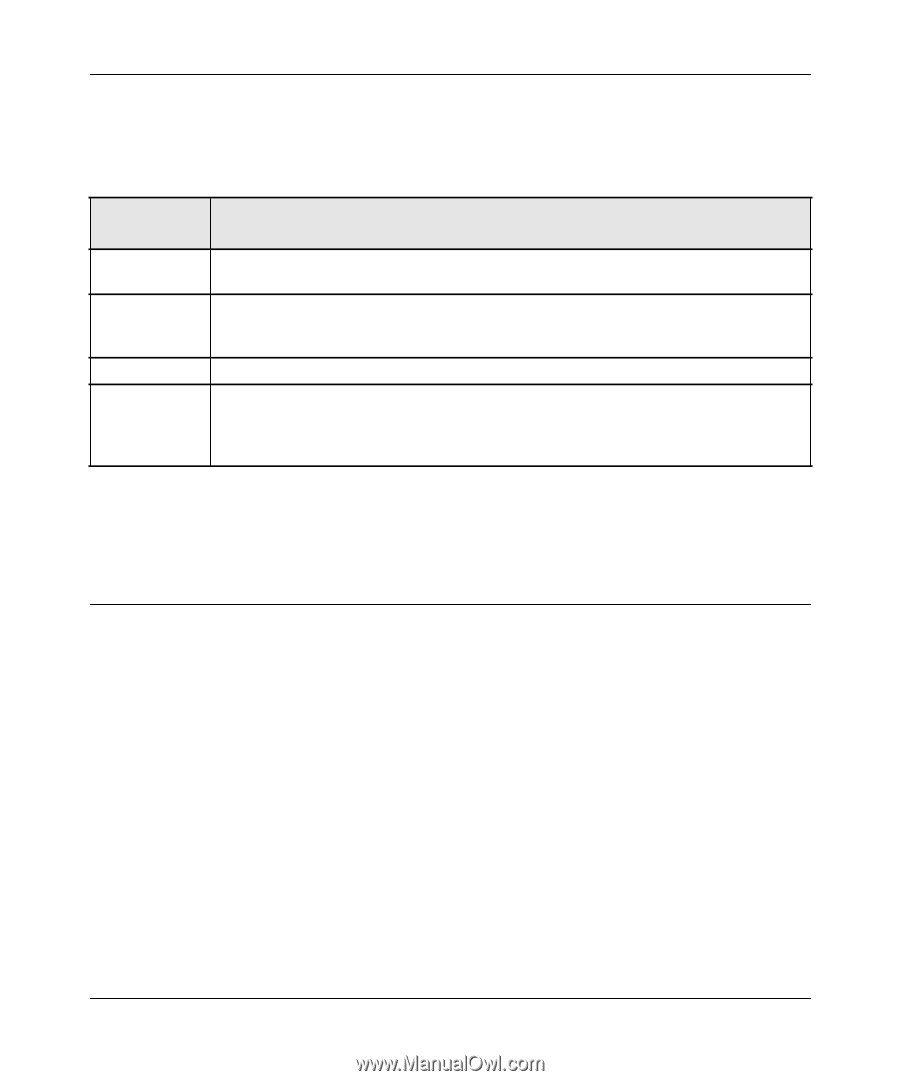
ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual When specifying RADIUS domain authentication, you are presented with several authentication protocol choices, as summarized in the following table: Table 6-1. Authentication Protocol Description PAP CHAP MIAS WiKID Password Authentication Protocol (PAP) is a simple protocol in which the client sends a password in clear text. Challenge Handshake Authentication Protocol (CHAP) executes a three-way handshake in which the client and server trade challenge messages, each responding with a hash of the other's challenge message that is calculated using a shared secret value. Network validated PAP or CHAP password based authentication scheme. WiKID is a PAP or CHAP key-based two-factor authentication method using public key cryptography. The client sends an encrypted PIN to the WiKID server and receives a onetime passcode with a short expiration period. The client logs in with the passcode. See tAppendix C, "Two Factor Authentication" for more on WiKID authentication. The chosen authentication protocol must be configured on the RADIUS server and on the authenticating client devices. Managing Certificates The FVS318G uses Digital Certificates (also known as X509 Certificates) during the Internet Key Exchange (IKE) authentication phase to authenticate connecting VPN gateways or clients, or to be authenticated by remote entities. The same Digital Certificates are extended for secure web access connections over HTTPS. Digital Certificates can be either self signed or can be issued by Certification Authorities (CA) such as via an in-house Windows server, or by an external organization such as Verisign or Thawte. However, if the Digital Certificates contain the extKeyUsage extension then the certificate must be used for one of the purposes defined by the extension. For example, if the Digital Certificate contains the extKeyUsage extension defined to SNMPV2 then the same certificate cannot be used for secure web management. The extKeyUsage would govern the certificate acceptance criteria in the FVS318G when the same digital certificate is being used for secure web management. Managing Users, Authentication, and Certificates 6-7 1.1 November, 2009