Netgear FVS318G FVS318G User Manual - Page 55
About Services-Based Rules, Outbound Rules (Service Blocking), Inbound Rules port forwarding
 |
UPC - 606449064827
View all Netgear FVS318G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
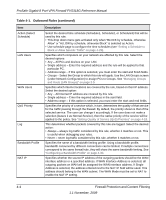
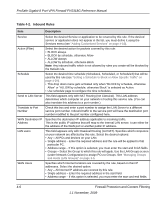
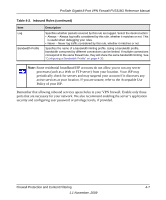
ProSafe Gigabit 8 Port VPN Firewall FVS318G Reference Manual About Services-Based Rules The rules to block traffic are based on the traffic's category of service. • Outbound Rules (service blocking). Outbound traffic is normally allowed unless the firewall is configured to disallow it. • Inbound Rules (port forwarding). Inbound traffic is normally blocked by the firewall unless the traffic is in response to a request from the LAN side. The firewall can be configured to allow this otherwise blocked traffic. • Customized Services. Additional services can be added to the list of services in the factory default list. These added services can then have rules defined for them to either allow or block that traffic (see "Adding Customized Services" on page 4-16. • Quality of Service (QoS) priorities. Each service at its own native priority that impacts its quality of performance and tolerance for jitter or delays. You can change this QoS priority if desired to change the traffic mix through the system (see "Setting Quality of Service (QoS) Priorities" on page 4-18). Outbound Rules (Service Blocking) The FVS318G allows you to block the use of certain Internet services by PCs on your network. This is called service blocking or port filtering. The default policy can be changed to block all outbound traffic and enable only specific services to pass through the router. The following Outbound Rules table lists the configured rules for outgoing traffic. An outbound rule is defined by the following fields: Table 4-1. Outbound Rules Item Service Name Action (Filter) Description Select the desired Service or application to be covered by this rule. If the desired service or application does not appear in the list, you must define it using the Services menu (see "Adding Customized Services" on page 4-16). Select the desired action for outgoing connections covered by this rule: • BLOCK always • BLOCK by schedule, otherwise Allow • ALLOW always • ALLOW by schedule, otherwise Block Note: Any outbound traffic which is not blocked by rules you create will be allowed by the Default rule. ALLOW rules are only useful if the traffic is already covered by a BLOCK rule. That is, you wish to allow a subset of traffic that is currently blocked by another rule. Firewall Protection and Content Filtering 4-3 1.1 November, 2009