HP 6125G HP 6125G & 6125G/XG Blade Switches Layer 3 - IP Services Conf - Page 60
Configuring DHCP snooping basic functions, Configuring DHCP snooping to support Option 82
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 60 highlights
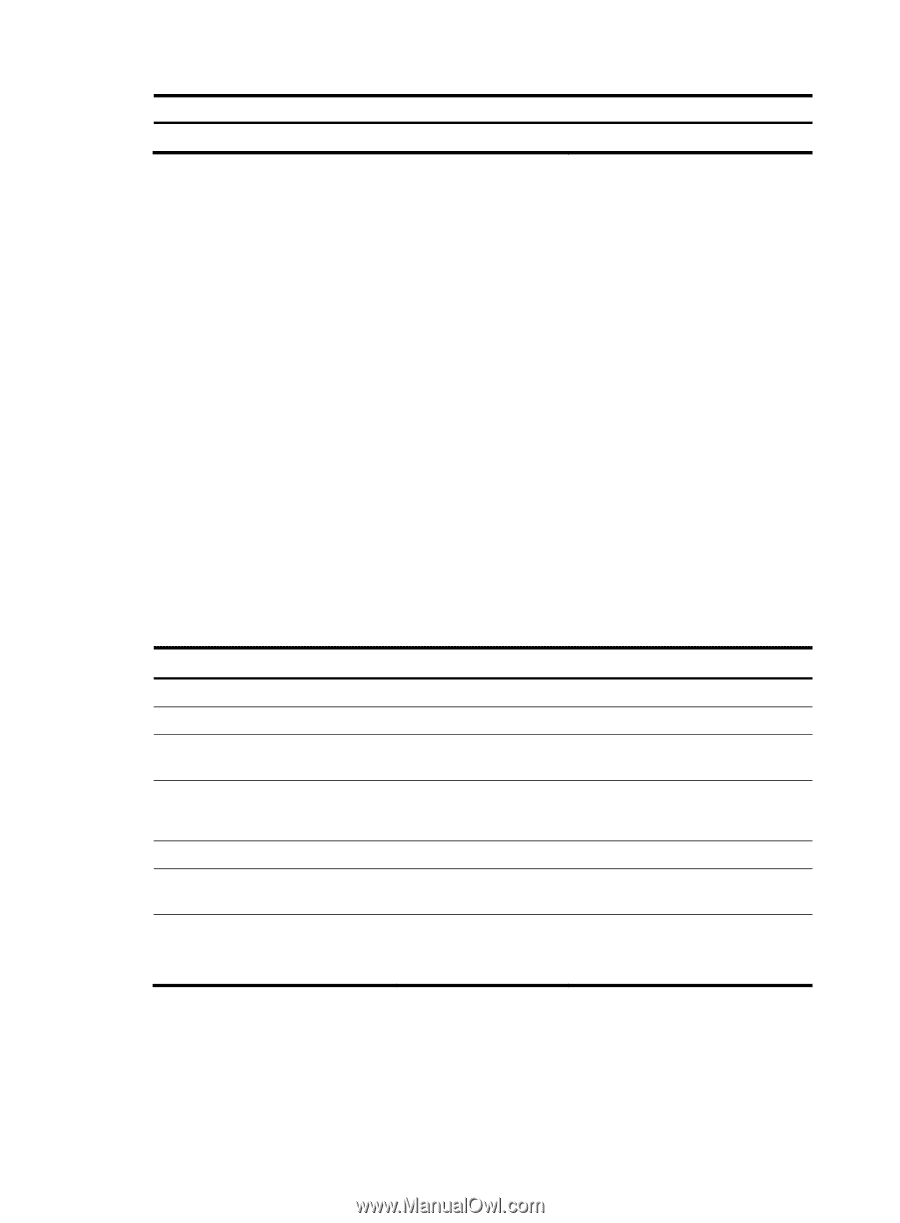
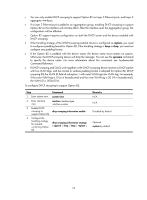
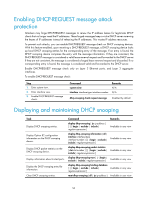
Task Enabling DHCP-REQUEST message attack protection Remarks Optional Configuring DHCP snooping basic functions Follow these guidelines when configure DHCP snooping basic functions: • You must specify the ports connected to the authorized DHCP servers as trusted to make sure that DHCP clients can obtain valid IP addresses. The trusted port and the port connected to the DHCP client must be in the same VLAN. • You can specify Layer 2 Ethernet ports and Layer 2 aggregate interfaces as trusted ports. For more information about aggregate interfaces, see Layer 2-LAN Switching Configuration Guide. • If a Layer 2 Ethernet port is added to an aggregation group, the DHCP snooping configuration of the interface will not take effect. After the interface quits the aggregation group, the configuration will be effective. • DHCP snooping can work with basic QinQ or flexible QinQ. When receiving a packet without any VLAN tag from the DHCP client to the DHCP server, the DHCP snooping device adds a VLAN tag to the packet. If the packet has one VLAN tag, the device adds another VLAN tag to the packet and records the two VLAN tags in a DHCP snooping entry. The newly added VLAN tag is the outer tag. If the packet has two VLAN tags, the device directly forwards the packet to the DHCP server without adding any tag. • If you need to add a new VLAN tag and meanwhile modify the original VLAN tag for the packet, DHCP snooping cannot work with flexible QinQ. To configure DHCP snooping basic functions: Step Command 1. Enter system view. 2. Enable DHCP snooping. system-view dhcp-snooping 3. Enter Ethernet interface view. 4. Specify the port as a trusted port that records the IP-to-MAC bindings of clients. 5. Return to system view. interface interface-type interface-number dhcp-snooping trust quit 6. Enter interface view. interface interface-type interface-number 7. Specify the port as a trusted port that does not record the IP-to-MAC dhcp-snooping trust bindings of clients. no-user-binding Remarks N/A Disabled by default. The interface connects to the DHCP server. After DHCP snooping is enabled, a port is an untrusted port by default. N/A The interface indirectly connects to the DHCP client. Optional. After DHCP snooping is enabled, a port is an untrusted port by default. Configuring DHCP snooping to support Option 82 Follow these guidelines when configure DHCP snooping to support Option 82: 52