Netgear GS752TP GS728TP/GS728TPP/GS752TP Software Administration Manual - Page 175
In the Source IP Address field, In the Service Type field
 |
View all Netgear GS752TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 175 highlights
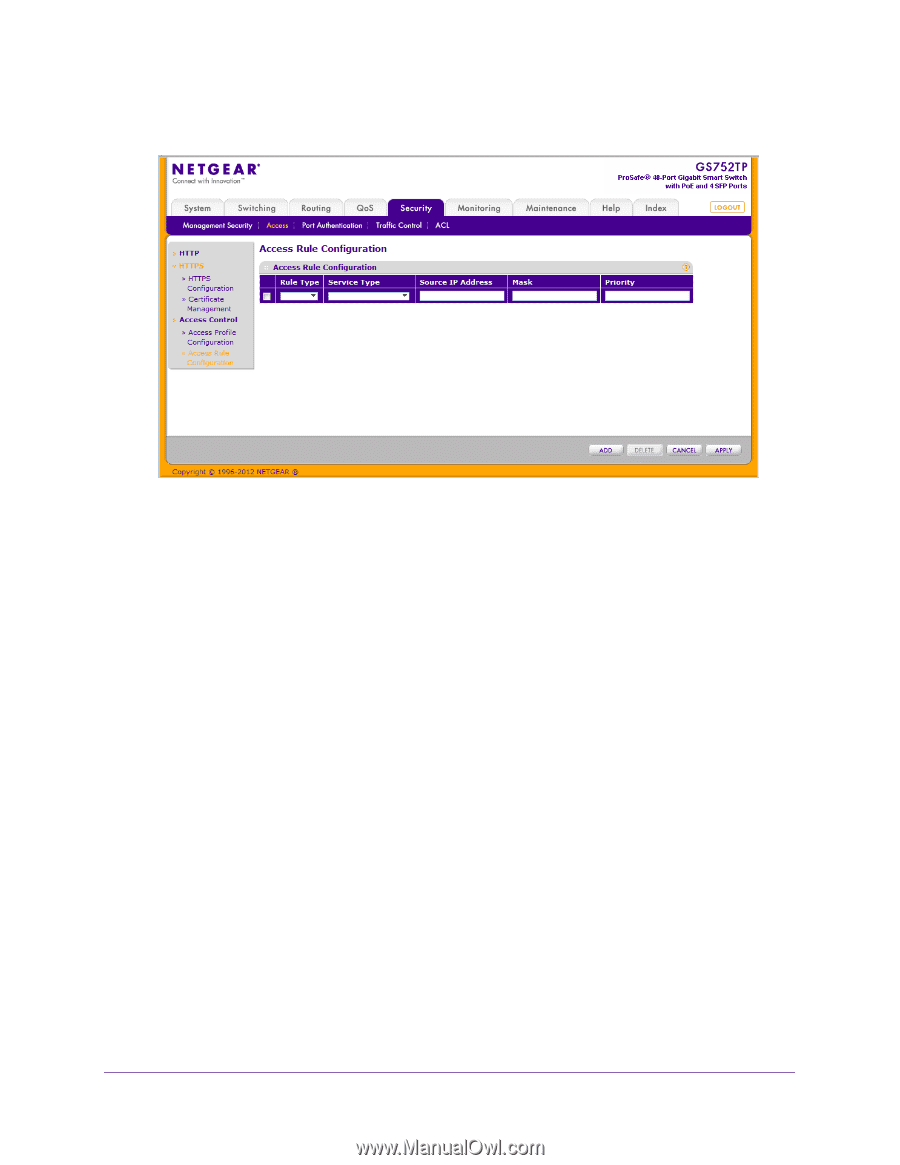
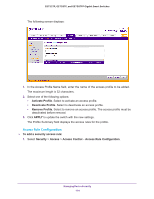
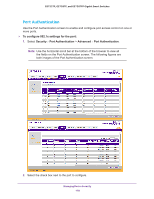
GS752TP, GS728TP, and GS728TPP Gigabit Smart Switches The following screen displays: 2. In the Rule Type field, select Permit or Deny as the action to be performed when the rule is matched. 3. In the Service Type field, select HTTP, Secure HTTP (SSL), or SNMP. The access rule is restricted according to the service type. 4. In the Source IP Address field, enter the IP address from which traffic is originated. 5. In the Mask field, enter the IP mask of the source IP addresses. 6. In the Priority field, enter a priority for the rule. The rules are validated against an incoming management request in the ascending order of their priorities. When a rule match is detected, the rule action is performed and subsequent rules are ignored. For example, if a source IP 10.10.10.10 is configured with priority 1 to permit, and source IP 10.10.10.10 is configured with priority 2 to deny, then access is permitted if the profile is active, and the second rule is ignored. 7. Click ADD. Make sure that the access profile is created before adding the rules. To configure a security access rule: 1. Select the checkbox next to the security access rule to be modified. 2. Update the relevant fields. 3. Click APPLY to update the switch with the new settings. Managing Device Security 175