Netgear GS752TP GS728TP/GS728TPP/GS752TP Software Administration Manual - Page 193
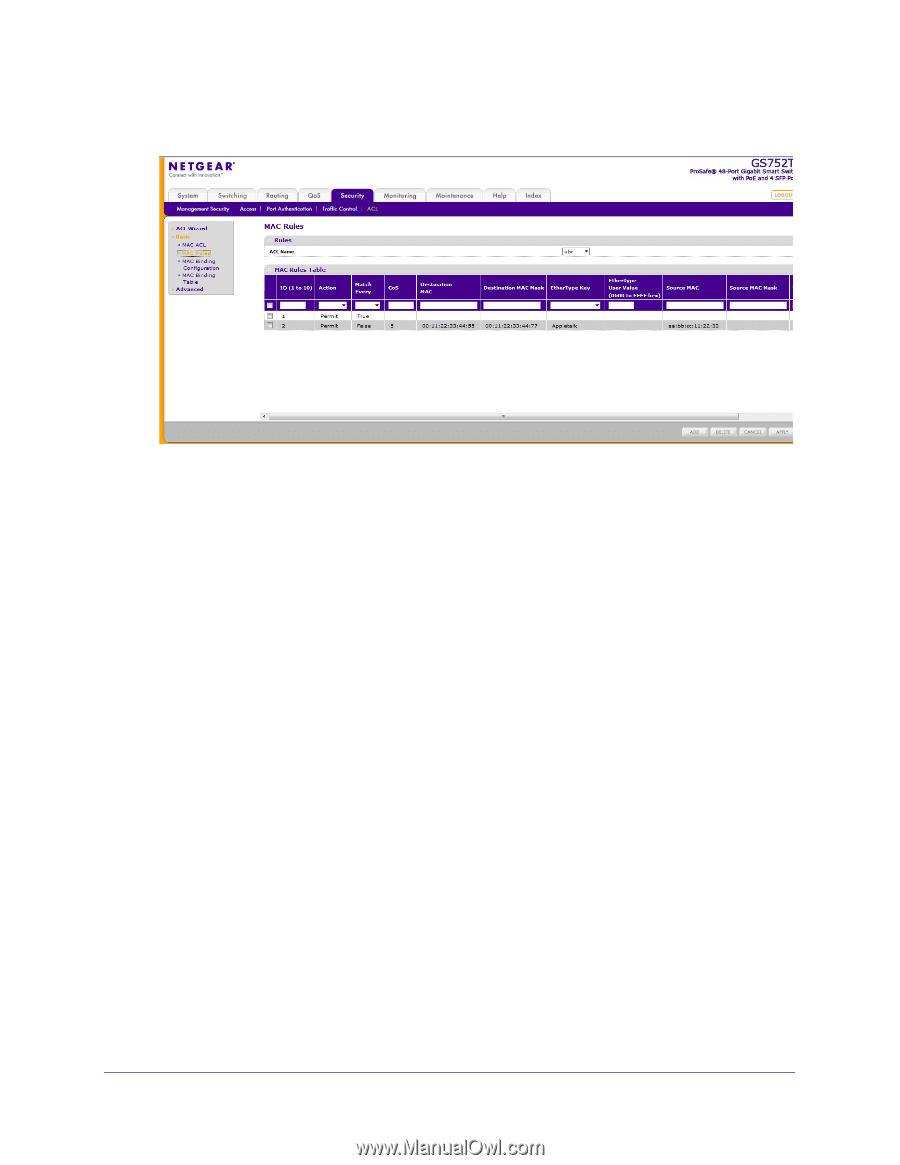
Action, Permit, Match Every, Enable, Disable, Destination MAC, xx:xx:xx:xx:xx:xx.
 |
View all Netgear GS752TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 193 highlights
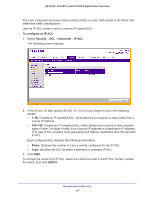
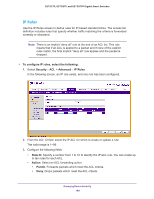
GS752TP, GS728TP, and GS728TPP Gigabit Smart Switches The following screen displays: 2. From the ACL Name field, specify the existing MAC ACL to which the rule applies. For information about how to set up a new MAC ACL, use the MAC ACL screen. 3. In the ID field, enter an ID for the rule. The valid range is 1-10. 4. Configure the following settings: • Action. Specify what action must be taken if a packet matches the rule's criteria. • Permit. Forwards packets that meet the ACL criteria. • Deny. Drops packets that meet the ACL criteria. • Match Every. Requires a packet to match the criteria of this ACL. Select Enable or Disable. Match Every is exclusive to the other filtering rules, so if Match Every is True, the other rules on the screen are not available. • CoS. Requires a packet's Class of Service (CoS) to match the CoS value listed here. Enter a CoS value between 0-7 to apply this criteria. • Destination MAC. Requires an Ethernet frame's destination port MAC address to match the address listed here. Enter a MAC address in this field. The valid format is xx:xx:xx:xx:xx:xx. • Destination MAC Mask. If desired, enter the MAC mask associated with the destination MAC to match. The MAC address mask specifies which bits in the destination MAC to compare against an Ethernet frame. Use Fs and 0s in the MAC mask, which is in a wildcard format. An F means that the bit is not checked, and a 0 in a bit position means that the data must equal the value given for that bit. For example, if the MAC address is aa:bb:cc:dd:ee:ff, and the mask is 00:00:ff:ff:ff:ff, all MAC addresses with aa:bb:xx:xx:xx:xx result in a match (where x is any hexadecimal number). A MAC mask of 00:00:00:00:00:00 matches a single MAC address. Managing Device Security 193