Cisco 7921G Administration Guide - Page 25
Identifying Encrypted and Authenticated Phone Calls, Security Restrictions - settings locked
 |
UPC - 882658123108
View all Cisco 7921G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
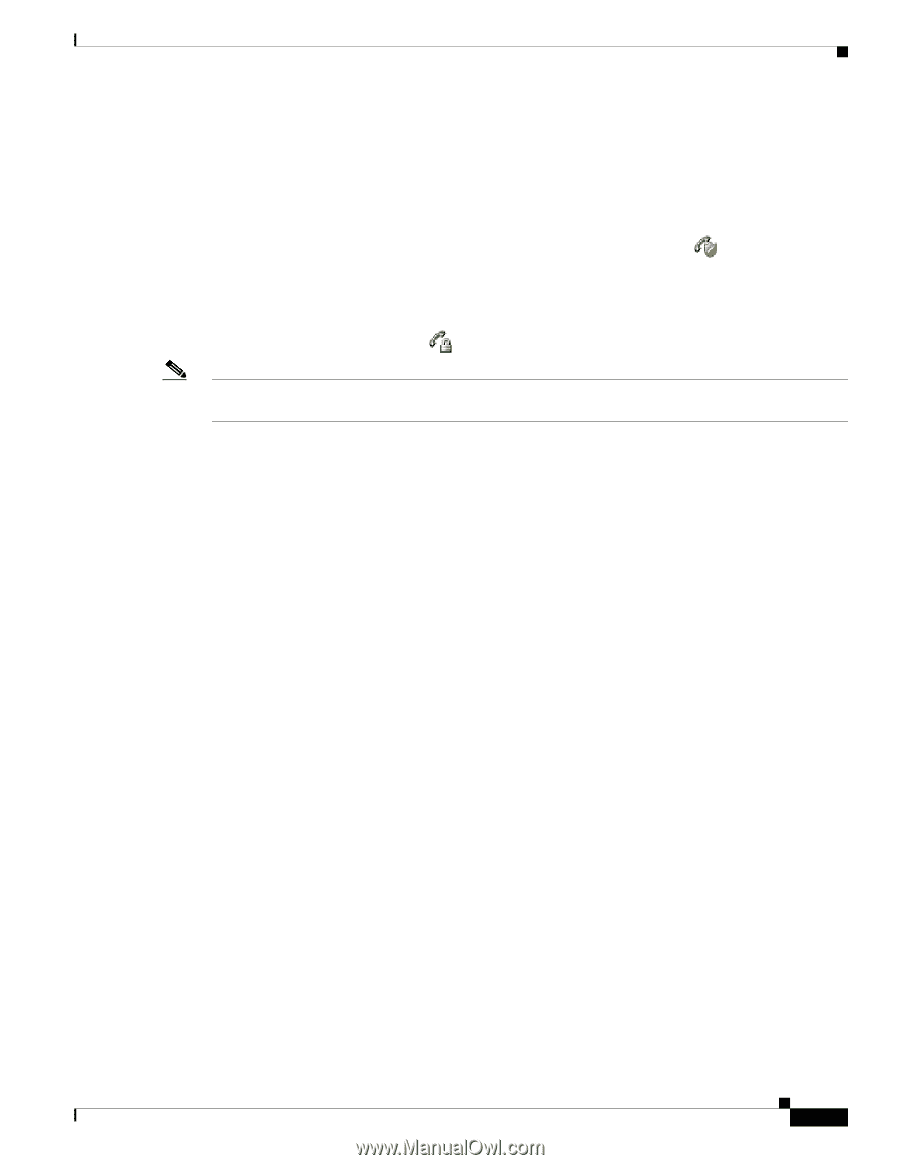
Chapter 1 Overview of the Cisco Unified Wireless IP Phone 7921G Overview of Configuring and Installing the Cisco Unified Wireless IP Phone 7921G Identifying Encrypted and Authenticated Phone Calls When security is implemented for a phone, you can identify authenticated or encrypted phone calls by icons on the screen on the phone. In an authenticated call, all devices participating in the establishment of the call are authenticated by the Cisco Unified Communications Manager. When a call in progress is authenticated, the call progress icon to the right of the call duration timer in the phone screen changes to this icon: In an encrypted call, all devices participating in the establishment of the call are authenticated by the Cisco Unified Communications Manager. In addition, call signaling and media streams are encrypted. An encrypted call offers the highest level of security, providing integrity and privacy to the call. When a call in progress is being encrypted, the call progress icon to the right of the call duration timer in the phone screen changes to this icon: Note If the call is routed through non-IP call legs, such as the PSTN, the call might be non-secure even though it is encrypted within the IP network and has a lock icon associated with it. Related Topics • Understanding Security Features for Cisco Unified IP Phones, page 1-7 • Understanding Security Profiles, page 1-10 • Security Restrictions, page 1-11 Security Restrictions When using a phone that is not configured for encryption, the user cannot barge into an encrypted call. When barge fails in this case, a reorder tone (fast busy tone) plays on the barge initiator's phone. If the phone is configured for encryption, the user can barge into an authenticated or non-secure call from the encrypted phone. After the barge occurs, Cisco Unified Communications Manager classifies the call as non-secure. If the phone is configured for encryption, the user can barge into an encrypted call, and the phone indicates that the call is encrypted. A user can barge into an authenticated call, even if the phone that is used to barge is non-secure. The authentication icon continues to display on the authenticated phones in the call, even if the initiator's phone does not support security. Overview of Configuring and Installing the Cisco Unified Wireless IP Phone 7921G When deploying a new IP telephony system, system administrators and network administrators must complete several initial configuration tasks to prepare the network for IP telephony service. For information and a checklist for setting up and configuring a complete Cisco IP telephony network, refer to the "System Configuration Overview" chapter in the Cisco Unified Communications Manager System Guide. OL-15985-01 Cisco Unified Wireless IP Phone 7921G Administration Guide for Cisco Unified Communications Manager Release 7.0 1-11