Netgear DGND3300v2 User Manual - Page 101
Using Auto Policy to Con VPN Tunnels, Configuring VPN Network Connection Parameters
 |
View all Netgear DGND3300v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 101 highlights
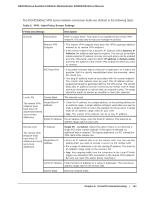
N300 Wireless Dual Band ADSL2+ Modem Router DGND3300v2 User Manual • Manual Policy. For a manual keying setup in which you must specify each phase of the connection, see Using Manual Policy to Configure VPN Tunnels on page 109. Manual policy does not use IKE. Rather, you manually enter all the authentication and key parameters. You have more control over the process; however, the process is more complex, and there are more opportunities for errors or configuration mismatches between your N300 Wireless Dual Band ADSL2+ Modem Router DGND3300v2 and the corresponding VPN endpoint gateway or client workstation. Using Auto Policy to Configure VPN Tunnels You need to configure matching VPN settings on both VPN endpoints. The outbound VPN settings on one end must match to the inbound VPN settings on other end, and vice versa. For an example of using Auto Policy, see Example of Using Auto Policy on page 106. Configuring VPN Network Connection Parameters All VPN tunnels on the N300 wireless modem router require that you configure several network parameters. This section describes those parameters and how to access them. The most common configuration scenarios use IKE to manage the authentication and encryption keys. The IKE protocol performs negotiations between the two VPN endpoints to automatically generate and update the required encryption parameters. Chapter 6. Virtual Private Networking | 101