Netgear DGND3300v2 User Manual - Page 79
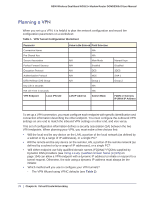
VPN Tunnel Configuration, Table 2., Parameters Recommended by the VPNC and Used in the VPN Wizard
 |
View all Netgear DGND3300v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 79 highlights
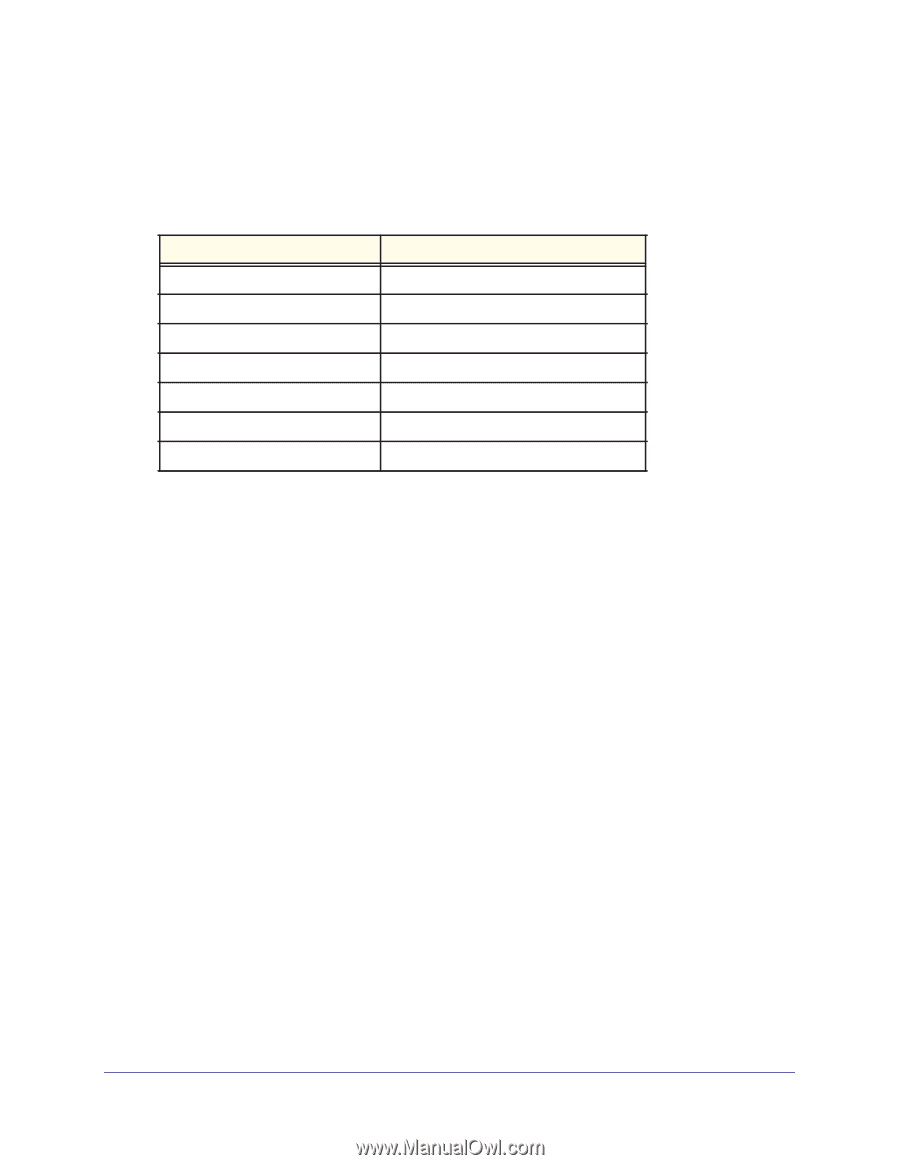
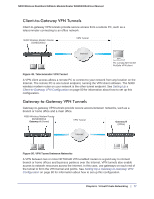
N300 Wireless Dual Band ADSL2+ Modem Router DGND3300v2 User Manual - The typical automated Internet Key Exchange (IKE) setup (see Using Auto Policy to Configure VPN Tunnels on page 101) - A manual keying setup in which you must specify each phase of the connection (see Using Manual Policy to Configure VPN Tunnels on page 109) Table 2. Parameters Recommended by the VPNC and Used in the VPN Wizard Parameter Secure Association Authentication Method Encryption Method Authentication Protocol Diffie-Hellman (DH) Group Key Life IKE Life Time Factory Default Setting Main Mode Pre-Shared Key 3DES SHA-1 Group 2 (1024 bit) 8 hours 1 hour • What level of IPSec VPN encryption will you use? - DES. The Data Encryption Standard (DES) processes input data that is 64 bits wide, encrypting these values using a 56-bit key. Faster but less secure than 3DES. - 3DES. Triple DES achieves a higher level of security by encrypting the data three times using DES with three different, unrelated keys. • What level of authentication will you use? - MDS. 128 bits, faster but less secure. - SHA-1. 160 bits, slower but more secure. VPN Tunnel Configuration There are two tunnel configurations and three ways to configure them: • Use the VPN Wizard to configure a VPN tunnel (recommended for most situations): - See Setting Up a Client-to-Gateway VPN Configuration on page 80. - See Setting Up a Gateway-to-Gateway VPN Configuration on page 90. • See Using Auto Policy to Configure VPN Tunnels on page 101 when the VPN Wizard and its VPNC defaults (see Table 2 on page 79) are not appropriate for your special circumstances, but you want to automate the Internet Key Exchange (IKE) setup. • See Using Manual Policy to Configure VPN Tunnels on page 109 when the VPN Wizard and its VPNC defaults (see Table 2 on page 79) are not appropriate for your special circumstances and you must specify each phase of the connection. You manually enter all the authentication and key parameters. You have more control over the process; however, the process is more complex, and there are more opportunities for errors or Chapter 6. Virtual Private Networking | 79