Netgear GS110TP GS108T/ GS110TP Smart Switch Software Administration Manual - Page 149
Server Address, Authentication Port, Secret Con d, Secret, Active, Message Authenticator, Apply
 |
UPC - 606449069129
View all Netgear GS110TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 149 highlights
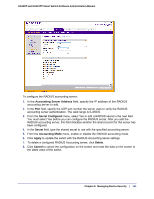
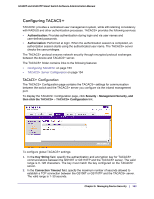
GS108T and GS110TP Smart Switch Software Administration Manual To configure a RADIUS server: 1. To add a RADIUS server, specify the settings the following list describes, and click Add. • In the Server Address field, specify the IP address of the RADIUS server to add. • In the Authentication Port field, specify the UDP port number the server uses to verify the RADIUS server authentication. The valid range is 0-65535. • From the Secret Configured menu, select Yes to add a RADIUS secret in the next field. You must select Yes before you can configure the RADIUS secret. After you add the RADIUS server, this field indicates whether the shared secret for this server has been configured. • In the Secret field, type the shared secret text string used for authenticating and encrypting all RADIUS communications between the switch and the RADIUS server. This secret must match the RADIUS encryption. • From the Active menu, specify whether the server is a Primary or Secondary server. • From the Message Authenticator menu, enable or disable the message authenticator attribute for the selected server. 2. To modify settings for a RADIUS server that is already configured on the switch, select the check box next to the server address, update the desired fields, and click Apply. 3. Click Refresh to update the page with the most current information. 4. To delete a configured RADIUS server, select the check box next to the server address, and then click Delete. 5. Click Cancel to cancel the configuration on the screen and reset the data on the screen to the latest value of the switch. The following table describes the RADIUS server statistics available on the page. Field Server Address Round Trip Time Description This displays all configured RADIUS servers. The time interval, in hundredths of a second, between the most recent Access-Reply/Access-Challenge and the Access-Request that matched it from this RADIUS authentication server. Chapter 5: Managing Device Security | 149