Netgear GS110TP GS108T/ GS110TP Smart Switch Software Administration Manual - Page 182
MAC ACL, Security, ACL. The MAC ACL is under the Basic, link., Rules, Direction, Delete, Apply.
 |
UPC - 606449069129
View all Netgear GS110TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 182 highlights
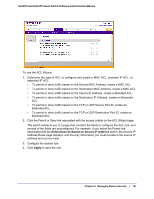
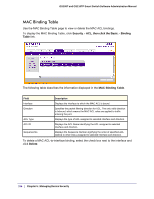
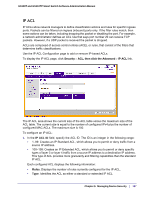
GS108T and GS110TP Smart Switch Software Administration Manual MAC ACL A MAC ACL consists of a set of rules which are matched sequentially against a packet. When a packet meets the match criteria of a rule, the specified rule action (Permit/Deny) is taken and the additional rules are not checked for a match. There are multiple steps involved in defining a MAC ACL and applying it to the switch: 1. Use the MAC ACL page to create the ACL ID. 2. Use the MAC Rules page to create rules for the ACL. 3. Use the MAC Binding Configuration page to assign the ACL by its ID number to a port. 4. Optionally, use the MAC Binding Table page to view the configurations. To display the MAC ACL page, click Security ACL. The MAC ACL page is under the Basic link. The MAC ACL table displays the number of ACLs currently configured in the switch and the maximum number of ACLs that can be configured. The current size is equal to the number of configured IPv4 ACLs plus the number of configured MAC ACLs. To configure a MAC ACL: 1. To add a MAC ACL, specify a name for the MAC ACL in the Name field, and click Add. The name string may include alphabetic, numeric, dash, underscore, or space characters only. The name must start with an alphabetic character. Each configured ACL displays the following information: • Rules. Displays the number of rules currently configured for the MAC ACL. • Direction. Displays the direction of packet traffic affected by the MAC ACL, which can be Inbound or blank. 2. To delete a MAC ACL, select the check box next to the Name field, then click Delete. 3. To change the name of a MAC ACL, select the check box next to the Name field, update the name, then click Apply. 182 | Chapter 5: Managing Device Security