Netgear GS110TP GS108T/ GS110TP Smart Switch Software Administration Manual - Page 155
Authentication List Configuration, Priority, Key String, Connection Timeout, Apply, TACACS, Server
 |
UPC - 606449069129
View all Netgear GS110TP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 155 highlights
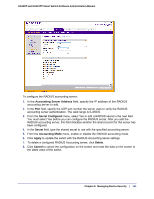
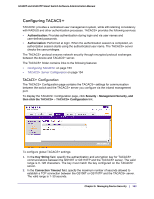
GS108T and GS110TP Smart Switch Software Administration Manual 2. In the Priority field, specify the order in which the TACACS+ servers are used. A value of 0 is the highest priority. 3. In the Port field, specify the authentication port number through which the TACACS+ session occurs. The default is port 49, and the range is 0-65535. 4. In the Key String field, specify the authentication and encryption key for TACACS+ communications between the GS108T or GS110TP and the TACACS+ server. This key must match the encryption used on the TACACS+ server. The valid range is 0-128 characters. 5. In the Connection Timeout field, specify the amount of time that passes before the connection between the device and the TACACS+ server times out. The field range is from 1 to 30 seconds. 6. If you make changes to the page, or add a new entry, click Apply to apply the changes to the system. 7. To delete a configured TACACS+ server, select the IP address of the server from the TACACS+ Server drop down menu, and then click Delete. Authentication List Configuration Use the Authentication List page to configure the default login list. A login list specifies one or more authentication methods to validate switch or port access for the admin user. Note: Admin is the only user on the system and is assigned to a preconfigured list named defaultList, which you cannot delete. To access the Authentication List page, click Security Management Security, and then click the Authentication List link. To change the authentication method for the defaultList: 1. Select the check box next to the defaultList name Chapter 5: Managing Device Security | 155