D-Link DGS-3200-16 User Manual - Page 118
DHCP Server Screening, DHCP Screening Port Settings, DHCP Offer Filtering
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 118 highlights
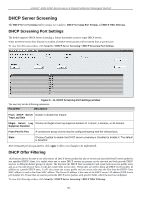
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch DHCP Server Screening The DHCP Server Screening folder contains two windows: DHCP Screening Port Settings and DHCP Offer Filtering. DHCP Screening Port Settings The Switch supports DHCP Server Screening, a feature that denies access to rogue DHCP servers. When the DHCP server filter function is enabled, all DHCP server packets will be filtered from a specific port. To view the following window, click Security > DHCP Server Screening > DHCP Screening Port Settings: Figure 5 - 11. DHCP Screening Port Settings window The user may set the following parameters: Parameter Description From DHCP Server Enable or disable this feature. Trap Log State Illegal Server Log Choose an illegal server log suppress duration of 1 minute, 5 minutes, or 30 minutes. Suppress Duration From Port/To Port A consecutive group of ports may be configured starting with the selected port. State Choose Enabled to enable the DHCP server screening or Disabled to disable it. The default is Disabled. After setting the previous parameters, click Apply to allow your changes to be implemented. DHCP Offer Filtering This function allows the user to not only restrict all DHCP Server packets but also to receive any specified DHCP server packet by any specified DHCP client, it is useful when one or more DHCP servers are present on the network and both provide DHCP services to different distinct groups of clients. The first time the DHCP filter is enabled it will create both an access profile entry and an access rule per port entry, it will also create other access rules. These rules are used to block all DHCP server packets. In addition to a permit DHCP entry, it will also create one access profile and one access rule entry the first time the DHCP client MAC address is used as the client MAC address. The Source IP address is the same as the DHCP server's IP address (UDP source port number 67). These rules are used to permit the DHCP server packets with specific fields, which the user has configured. To view the following window, click Security > DHCP Server Screening > DHCP Offer Filtering: 105