D-Link DGS-3200-16 User Manual - Page 180
IPv4 DSCP, Source IP Mask, Destination IP Mask, Protocol
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 180 highlights
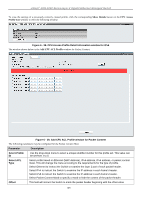
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch IPv4 DSCP Source IP Mask Destination IP Mask Protocol and use this as the, or part of the criterion for forwarding. Selecting this option instructs the Switch to examine the DiffServ Code part of each packet header and use this as the, or part of the criterion for forwarding. Enter an IP address mask for the source IP address. Enter an IP address mask for the destination IP address. Selecting this option instructs the Switch to examine the protocol type value in each frame's header. You must then specify what protocol(s) to include according to the following guidelines: Select ICMP to instruct the Switch to examine the Internet Control Message Protocol (ICMP) field in each frame's header. • Select Type to further specify that the access profile will apply an ICMP type value, or specify Code to further specify that the access profile will apply an ICMP code value. Select IGMP to instruct the Switch to examine the Internet Group Management Protocol (IGMP) field in each frame's header. • Select Type to further specify that the access profile will apply an IGMP type value. Select TCP to use the TCP port number contained in an incoming packet as the forwarding criterion. Selecting TCP requires a source port mask and/or a destination port mask is to be specified. The user may also identify which flag bits to filter. Flag bits are parts of a packet that determine what to do with the packet. The user may filter packets by filtering certain flag bits within the packets, by checking the boxes corresponding to the flag bits of the TCP field. The user may choose between urg (urgent), ack (acknowledgement), psh (push), rst (reset), syn (synchronize), fin (finish). • src port mask - Specify a TCP port mask for the source port in hex form (hex 0x00xffff), which you wish to filter. • dst port mask - Specify a TCP port mask for the destination port in hex form (hex 0x0-0xffff) which you wish to filter. Select UDP to use the UDP port number contained in an incoming packet as the forwarding criterion. Selecting UDP requires that you specify a source port mask and/or a destination port mask. • src port mask - Specify a UDP port mask for the source port in hex form (hex 0x00xffff). • dst port mask - Specify a UDP port mask for the destination port in hex form (hex 0x0-0xffff). Protocol id - Enter a value defining the protocol ID in the packet header to mask. Specify the protocol ID mask in hex form (hex 0x0-0xff). Use the following command on the CLI: "DGS3200-10:4#create access_profile profile_id 1 ip protocol_id_mask 0xFF user_define_mask ". Click Apply to set this entry in the Switch's memory. To view the settings of a previously correctly created profile, click the corresponding Show Details button on the CPU Access Profile List window to view the following window: Figure 6 - 26. CPU Access Profile Detail Information window for IP (IPv4) The window shown below is the Add CPU ACL Profile window for IPv6. 167