D-Link DGS-3200-16 User Manual - Page 149
Conditions and Limitations, WAC Global Settings
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 149 highlights
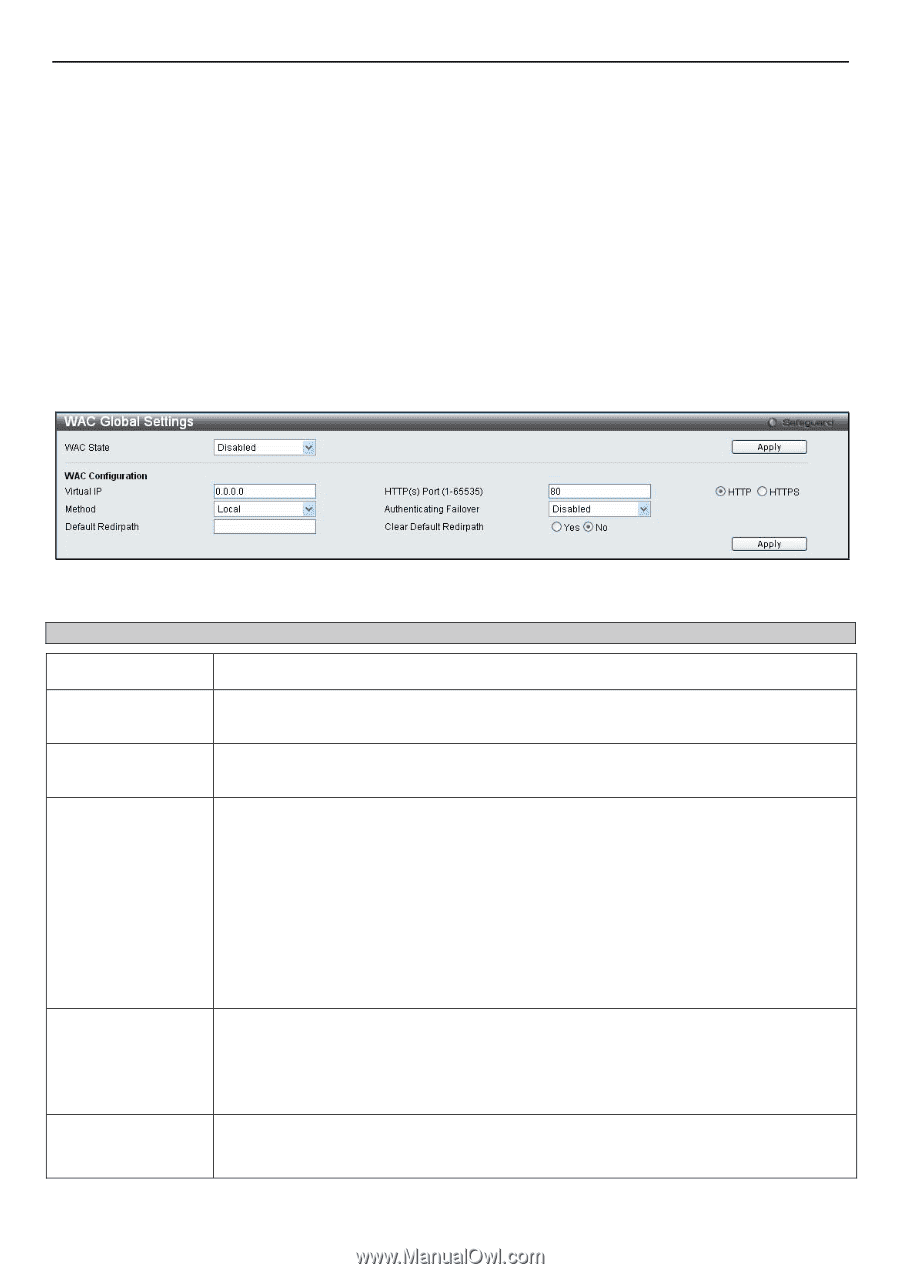
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Conditions and Limitations 1. If the client is utilizing DHCP to attain an IP address, the authentication VLAN must provide a DHCP server or a DHCP relay function so that client may obtain an IP address. 2. Certain functions exist on the Switch that will filter HTTP packets, such as the Access Profile function. The user needs to be very careful when setting filter functions for the target VLAN, so that these HTTP packets are not denied by the Switch. 3. If a RADIUS server is to be used for authentication, the user must first establish a RADIUS Server with the appropriate parameters, including the target VLAN, before enabling Web Authentication on the Switch. WAC Global Settings Users can configure the Switch for Web authentication. To view the following window, click Security > Web Authentication > WAC Global Settings: Figure 5 - 46. WAC Global Settings window To set the Web Authentication for the Switch, complete the following fields: Parameter Description WAC State Use this drop-down menu to either enable or disable the Web Authentication on the Switch. Virtual IP Enter a virtual IP address. This address is only used by WAC and is not known by any other modules of the Switch. HTTP(s) Port (165535) Enter a HTTP port number. Port 80 is the default. Method Use this drop-down menu to choose the authenticator for Web-based Access Control. The user may choose: Local - Choose this parameter to use the local authentication method of the Switch as the authenticating method for users trying to access the network via the switch. This is, in fact, the username and password to access the Switch configured using the WAC User Settings window (Security > Web Authentication > WAC User Settings) seen below. RADIUS - Choose this parameter to use a remote RADIUS server as the authenticating method for users trying to access the network via the switch. This RADIUS server must have already been pre-assigned by the administrator using the Authentic RADIUS Server window (Security > 802.1X > Authentic RADIUS Server). Authenticating Failover Redirection Page Toggle between Enabled and Disabled. This is used to configure WAC authentication failover. By default, the authentication failover is disabled. If RADIUS servers are unreachable, the authentication will fail. When the authentication failover is enabled, if RADIUS server authentication is unreachable, the local database will be used to do the authentication. Enter the URL of the website that authenticated users placed in the VLAN are directed to once authenticated. This path must be entered into this field before the Web-based Access Control can be enabled. 136