D-Link DGS-3200-16 User Manual - Page 168
Packet Content, Access Profile Detail Information window for Packet Content, Apply
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 168 highlights
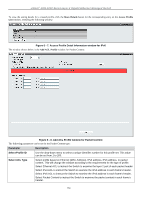
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Packet Content Allows users to examine up to four specified offset chunks within a packet, one at a time. A chunk mask presents four bytes. Four offset chunks can be selected from a possible 32 predefined offset chunks as described below: offset_chunk_1, offset_chunk_2, offset_chunk_3, offset_chunk_4. chunk0 chunk1 chunk2 ...... chunk29 chunk30 chunk31 B126, B2, B6, ...... B114, B118, B122, B127, B3, B7, B115, B119, B123, B0, B4, B8, B116, B120, B124, B1 B5 B9 B117 B121 B125 Example: offset_chunk_1 0 0xffffffff will match packet byte offset 126, 127, 0, 1 offset_chunk_1 0 0x0000ffff will match packet byte offset, 0,1 Note: Only one packet content mask profile can be created at a time. Use of the D-Link xStack switch family's advanced Packet Content Mask (also known as Packet Content Access Control List - ACL) feature can effectively mitigate common network attacks such as ARP Spoofing. The Switch's implementation of Packet Content ACL enables inspection of any packet's specified content regardless of the protocol layer. Click Apply to implement changes made. To view the setting details for a created profile, click the Show Details button for the corresponding entry on the Access Profile List window, revealing the following window: Figure 6 - 9. Access Profile Detail Information window for Packet Content NOTE: Address Resolution Protocol (ARP) is the standard for finding a host's hardware address (MAC address). However, ARP is vulnerable as it can be easily spoofed and utilized to attack a LAN (i.e. an ARP spoofing attack). For a more detailed explanation on how ARP protocol works and how to employ D-Link's unique Packet Content ACL to prevent ARP spoofing attack, please see Appendix E at the end of this manual. To establish the rule for a previously created Access Profile: To configure the Access Rules for Ethernet, open the Access Profile List window and click Add/View Rules for an Ethernet entry. This will open the following window: 155