D-Link DGS-3200-16 User Manual - Page 142
Login Method Lists, Enable Admin, Security > Access Authentication Control > Login Method Lists
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 142 highlights
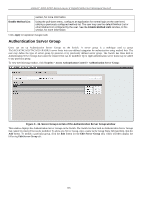
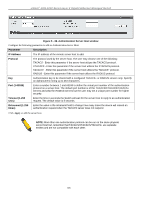
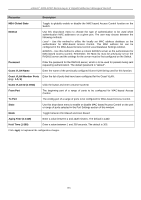
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch Login Method Lists User-defined or default Login Method List of authentication techniques can be configured for users logging on to the Switch. The sequence of techniques implemented in this command will affect the authentication result. For example, if a user enters a sequence of techniques, for example TACACS - XTACACS- local, the Switch will send an authentication request to the first TACACS host in the server group. If no response comes from the server host, the Switch will send an authentication request to the second TACACS host in the server group and so on, until the list is exhausted. At that point, the Switch will restart the same sequence with the following protocol listed, XTACACS. If no authentication takes place using the XTACACS list, the local account database set in the Switch is used to authenticate the user. When the local method is used, the privilege level will be dependant on the local account privilege configured on the Switch. Successful login using any of these techniques will give the user a "User" privilege only. If the user wishes to upgrade his or her status to the administrator level, the user must use the Enable Admin window, in which the user must enter a previously configured password, set by the administrator. To view the following window, click Security > Access Authentication Control > Login Method Lists: Figure 5 - 39. Login Method Lists window The Switch contains one Method List that is set and cannot be removed, yet can be modified. To delete a Login Method List defined by the user, click the Delete button corresponding to the entry desired to be deleted. To modify a Login Method List, click on its corresponding Edit button.. To define a Login Method List, set the following parameters and click Apply: Parameter Description Method List Name Enter a method list name defined by the user of up to 15 characters. Priority 1, 2, 3, 4 The user may add one, or a combination of up to four of the following authentication methods to this method list: tacacs - Adding this parameter will require the user to be authenticated using the TACACS protocol from a remote TACACS server. xtacacs - Adding this parameter will require the user to be authenticated using the XTACACS protocol from a remote XTACACS server. tacacs+ - Adding this parameter will require the user to be authenticated using the TACACS+ protocol from a remote TACACS+ server. radius - Adding this parameter will require the user to be authenticated using the RADIUS protocol from a remote RADIUS server. local - Adding this parameter will require the user to be authenticated using the local user account database on the Switch. none - Adding this parameter will require no authentication to access the Switch. 129