D-Link DGS-3200-16 User Manual - Page 127
X User, Capability, Direction, X User window - 24 firmware
 |
UPC - 790069312007
View all D-Link DGS-3200-16 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 127 highlights
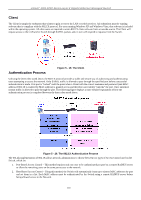
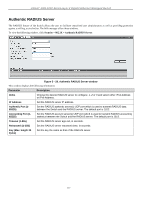
xStack® DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch attempts by the client to authenticate. The Switch cannot provide authentication services to the client through the interface. If Auto is selected, it will enable 802.1X and cause the port to begin in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. The authentication process begins when the link state of the port transitions from down to up, or when an EAPOLstart frame is received. The Switch then requests the identity of the client and begins relaying authentication messages between the client and the authentication server. The default setting is Auto. Capability This allows the 802.1X Authenticator settings to be applied on a per-port basis. Select Authenticator to apply the settings to the port. When the setting is activated, a user must pass the authentication process to gain access to the network. Select None disable 802.1X functions on the port. Direction Sets the administrative-controlled direction to Both. If Both is selected, control is exerted over both incoming and outgoing traffic through the controlled port selected in the first field. The In option is not supported in the present firmware release. Click Apply to implement your configuration changes. 802.1X User Users can set different local users on the Switch. To view the following window, click Security > 802.1X > 802.1X User: Figure 5 - 24. 802.1X User window Enter an 802.1X user name, Password, and confirmation of that password. Properly configured local users will be displayed in the 802.1X User Table at the bottom of the window. Click Apply to implement your configuration changes. 114