Cisco 7925G Administration Guide - Page 89
Configuring Wireless LAN Security, Authentication Mode, Wireless Encryption
 |
UPC - 882658201943
View all Cisco 7925G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 89 highlights
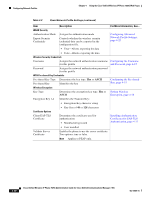
Chapter 4 Using the Cisco Unified Wireless IP Phone 7925G Web Pages Configuring Network Profiles Configuring Wireless LAN Security The Cisco Unified Wireless IP Phone 7925G supports many types of authentication. Authentication methods might require a specific encryption method or you can choose between several encryption methods. When configuring a network profile, you can choose one of these authentication methods: • Open-Provides access to all access points without WEP Key authentication/encryption. • Open plus WEP-Provides access to all access points and authentication through the use of one or more WEP Keys at the local access point. • Shared Key plus WEP-Provides shared key authentication through the use of WEP Keys at the local access point. • LEAP- Exchanges a username and cryptographically secure password with a RADIUS server for authentication in the network. LEAP is a Cisco proprietary version of EAP. • EAP-FAST-Exchanges a username and password and with a RADIUS server for authentication in the network. • EAP-TLS-Uses a dynamic session-based WEP key derived from the client adapter and RADIUS server to encrypt data and a client certificate for authentication. It uses PKI to secure communication to the RADIUS authentication server. • PEAP (EAP-MSCHAP V2)-Performs mutual authentication, but does not require a client certificate on the phone. This method uses name and password authentication based on Microsoft MSCHAP V2 authentication. • PEAP with Server Certificate Authentication-The Cisco Unified Wireless IP Phone 7925G can validate the server certificate during the authentication handshakes over an 802.11 wireless link. This functionality is disabled by default and is enabled in Cisco Unified Communications Manager Administration. • Auto (AKM)-Automatic authenticated key management in which the phone selects the AP and type of key management scheme, which includes WPA, WPA2, WPA-Pre-shared key, WPA2-Pre-shared key, or CCKM (which uses a wireless domain server (WDS)). Note When set to AKM mode, the phone uses LEAP for 802.1x type authentication methods (non-Pre-shared key such as WPA, WPA2, or CCKM). AKM mode supports only authenticated key-management types (WPA, WPA2, WPA-PSK, WPA2-PSK, CCKM). The type of authentication and encryption schemes that you are using with your WLAN determine how you set up the authentication, security, and encryption options in the network profiles for the Cisco Unified Wireless IP Phones. Table 4-5 provides a list of supported authentication and encryption schemes that you can configure on the Cisco Unified Wireless IP Phone 7925G. Table 4-5 Authentication and Encryption Configuration Options Authentication Mode Open Open plus WEP Shared Key plus WEP Wireless Encryption None Static WEP Requires WEP Key Static WEP Requires WEP Key Wireless Security Credentials None-access to all APs None-access to all APs Uses shared-key with AP OL-15984-01 Cisco Unified Wireless IP Phone 7925G Administration Guide for Cisco Unified Communications Manager 7.0(1) 4-13