Cisco 7925G Administration Guide - Page 90
Configuring the Authentication Mode
 |
UPC - 882658201943
View all Cisco 7925G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 90 highlights
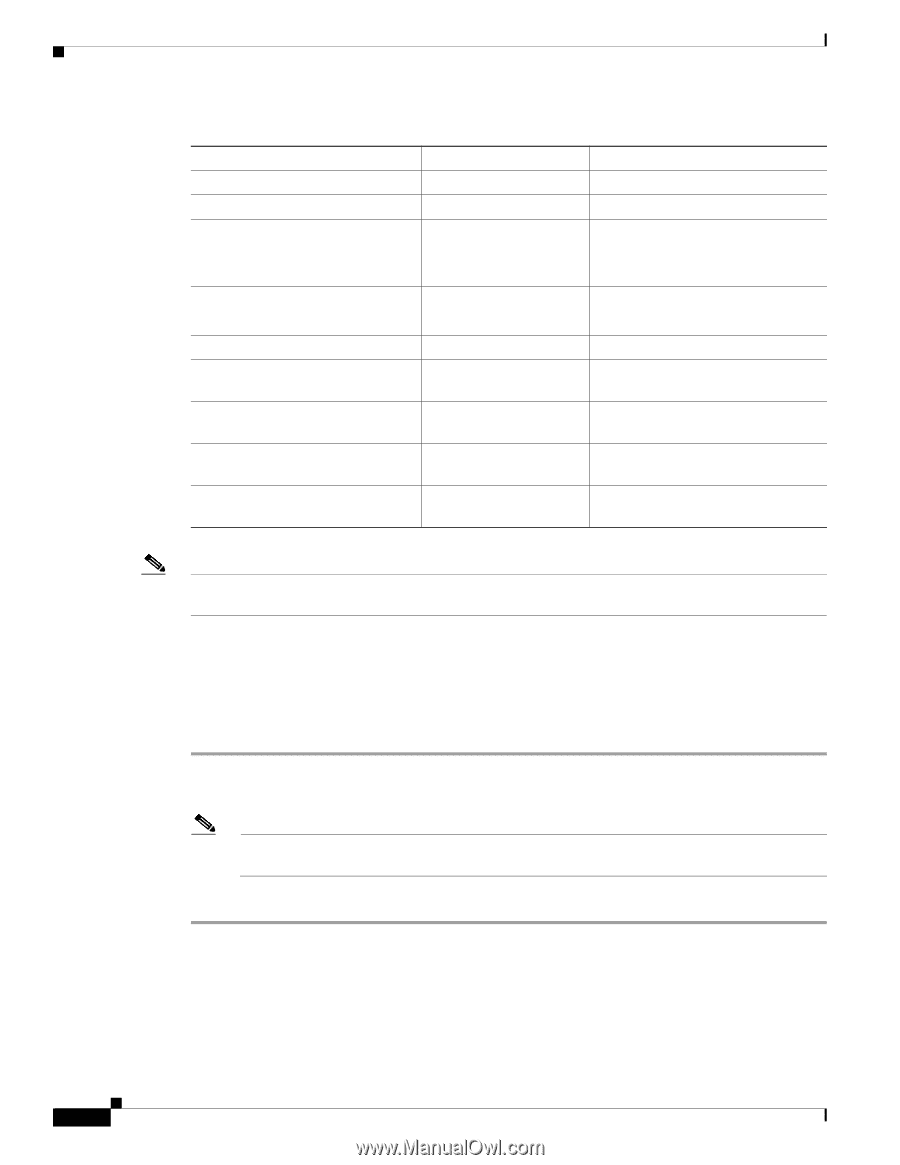
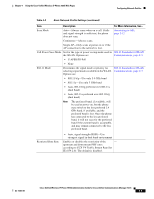
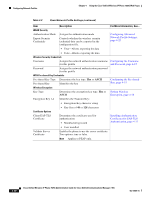
Configuring Network Profiles Chapter 4 Using the Cisco Unified Wireless IP Phone 7925G Web Pages Table 4-5 Authentication and Encryption Configuration Options (continued) Authentication Mode Wireless Encryption Wireless Security Credentials LEAP (with optional CCKM) Uses WEP Requires Username and Password EAP-FAST (with optional CCKM) Uses WEP or TKIP Requires Username and Password EAP-TLS Uses WEP, TKIP, or AES Requires Username and Password Requires server and client certificates. PEAP Uses WEP, TKIP, or AES Requires Username and Password Requires server side certificate. Auto (AKM) with CCKM Uses TKIP or AES Requires Username and Password Auto (AKM) with WPA (with optional CCKM) Uses TKIP Requires Username and Password Auto (AKM) with WPA2 (with optional CCKM) Uses AES Requires Username and Password Auto (AKM) with WPA Pre-Shared Uses TKIP Key Requires Passphrase Auto (AKM) with WPA2 Pre-Shared Key Uses AES Requires Passphrase Note Beginning with Cisco Wireless IP Phone 7925G firmware release 1.1, CCKM is operational with the WPA authentication mode using AES encryption. Configuring the Authentication Mode To select the Authentication Mode for this profile, follow these steps: Procedure Step 1 Choose the network profile that you want to configure. Step 2 Choose the authentication mode. Note Depending on what you selected, you must configure additional options in Wireless Security or Wireless Encryption. See Table 4-5 for more information. Step 3 Click Save to make the change. 4-14 Cisco Unified Wireless IP Phone 7925G Administration Guide for Cisco Unified Communications Manager 7.0(1) OL-15984-01