Netgear GS728TPP GS728TP/GS728TPP/GS752TP Software Administration Manual - Page 194
MAC Binding Configuration, EtherType User Value
 |
View all Netgear GS728TPP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 194 highlights
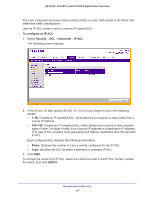
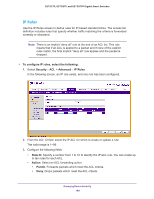
GS752TP, GS728TP, and GS728TPP Gigabit Smart Switches • EtherType Key. Requires a packet's EtherType to match the EtherType you select. Select the EtherType value from the drop-down list. If you select User Value, you can enter a custom EtherType value. • EtherType User Value. This field is configurable if you select User Value from the EtherType drop-down list. The value you enter specifies a customized EtherType to compare against an Ethernet frame. The valid range is 0x0600-0xFFFF. • Source MAC. Requires a packet's source port MAC address to match the address listed here. Enter a MAC address in this field. The valid format is xx:xx:xx:xx:xx:xx. • Source MAC Mask. If desired, enter the MAC mask for the source MAC address to match. Use Fs and 0s in the MAC mask, which is in a wildcard format. An F means that the bit is not checked, and a 0 in a bit position means that the data must equal the value given for that bit. The valid format is xx:xx:xx:xx:xx:xx. A MAC mask of 00:00:00:00:00:00 matches a single MAC address. • VLAN. Requires a packet's VLAN ID to match the ID listed here. Enter the VLAN ID to apply this criteria. The valid range is 1-4093. • Logging. Enables or disables logging of management access list (ACL) deny events. 5. Click ADD. To change a rule, select the check box associated with the rule, change the desired fields, and click APPLY. MAC Binding Configuration When an ACL is bound to an interface, all the rules that have been defined are applied to the selected interface. Use the MAC Binding Configuration screen to assign MAC ACL lists to ACL priorities and interfaces. To configure MAC ACL interface bindings: 1. Select Security ACL > Basic MAC Binding Configuration. Managing Device Security 194