HP Dc7100 HP Compaq Business Desktop dc7100 Series Service Reference Guide, 3r - Page 45
Asset Tracking and Security, Computer Setup Utilities F10 Security Features
 |
UPC - 829160356877
View all HP Dc7100 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 45 highlights
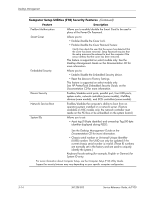
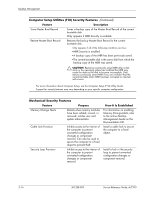
Desktop Management 3.4 Asset Tracking and Security Asset tracking features incorporated into the computer provide key asset tracking data that can be managed using HP Insight Manager, HP Client Manager or other system management applications. Seamless, automatic integration between asset tracking features and these products enables you to choose the management tool that is best suited to your environment and to leverage your investment in existing tools. HP also offers several solutions for controlling access to valuable components and information. ProtectTools Embedded Security, if installed, prevents unauthorized access to data and checks system integrity and authenticates third-party users attempting system access. (Refer to HP ProtectTools Embedded Security Guide, on the Documentation CD for more information.) Security features such as ProtectTools, the Smart Cover Sensor and the Smart Cover Lock, available on select models, help to prevent unauthorized access to the internal components of the personal computer. By disabling parallel, serial, or USB ports, or by disabling removable media boot capability, you can protect valuable data assets. Memory Change and Smart Cover Sensor alerts can be automatically forwarded to system management applications to deliver proactive notification of tampering with a computer's internal components. ✎ ProtectTools, the Smart Cover Sensor, and the Smart Cover Lock are available as options on select systems. Use the following utilities to manage security settings on your HP computer: ■ Locally, using the Computer Setup Utilities. See the Computer Setup (F10) Utility Guide included with the computer for additional information and instructions on using the Computer Setup Utilities. ■ Remotely, using HP Client Manager Software or System Software Manager. This software enables the secure, consistent deployment and control of security settings from a simple command-line utility. Computer Setup Utilities (F10) Security Features Feature Description Setup Password Allows you to set and enable setup (administrator) password. ✎ If the setup password is set, it is required to change Computer Setup options, flash the ROM, and make changes to certain plug and play settings under Windows. See the Troubleshooting Guide on the Documentation CD for more information. Power-On Password Allows you to set and enable power-on password. See the Troubleshooting Guide on the Documentation CD for more information. Password Options (This selection will appear only if a power-on password is set.) Allows you to specify whether the password is required for warm boot (CTRL+ALT+DEL). See the Desktop Management Guide on the Documentation CD for more information. ✎ For more information about Computer Setup, see the Computer Setup (F10) Utility Guide. Support for security features may vary depending on your specific computer configuration. Service Reference Guide, dc7100 361288-003 3-13