HP Integrity rx2800 HP Integrity iLO 3 Operations Guide - Page 129
Creating roles that follow organizational structure, Restricting roles
 |
View all HP Integrity rx2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 129 highlights
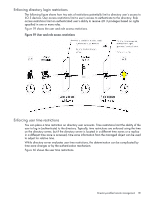
For example, an organization might have two types of users: administrators of the iLO 3 device or host server, and users of the iLO 3 device. In this situation, it makes sense to create two roles, one for the administrators and one for the users. Both roles include some of the same devices, but grant different rights. Sometimes, it is useful to assign generic rights to the lesser role, and include the iLO 3 administrators in that role, and the administrative role. Figure 57 shows one way that an administrative user gains admin role right. The admin user's initial login right is granted through the regular user role. After the initial login, more advanced rights are assigned to the admin user through the admin role such as server reset and remote console. Figure 57 Admin user gaining admin role right, example 1 In Figure 58, the admin user gains the admin role right in a different way. The admin user initially logs in through the admin role and is immediately assigned admin rights (server reset, remote console, and login). Figure 58 Admin user gaining admin role right, example 2 Creating roles that follow organizational structure Often, administrators within an organization are placed into a hierarchy in which subordinate administrators must assign rights independently of ranking administrators. In this case, it is useful to have one role that represents the rights assigned by higher-level administrators, and to enable subordinate administrators to create and manage their own roles. Restricting roles Restrictions enable you to limit the scope of a role. A role only grants rights to those users who satisfy the role restrictions. Using restricted roles creates users with dynamic rights that change based on the time of day or network address of the client. For step-by-step instructions on how to create network and time restrictions for a role, see "Setting role restrictions" (page 121) or "Setting time restrictions" (page 122). Directory-enabled remote management 129