Netgear WC7520 WC7520 Reference Manual - Page 83
Configuring Security and Wireless Security Profiles, Managing Wireless Security Profiles
 |
UPC - 606449072969
View all Netgear WC7520 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 83 highlights
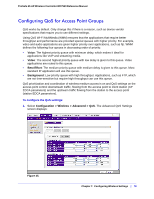
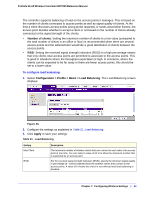
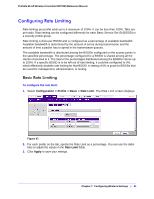
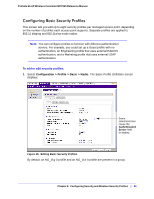
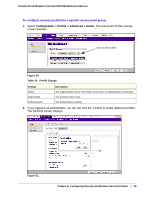
8. Configuring Security and Wireless Security Profiles 8 This chapter includes the following sections: • Managing Wireless Security Profiles on this page • Managing Rogue Access Points on page 89 • Managing MAC Authentication and MAC Authentication Groups on page 92 • Managing Authentication Servers and Authentication Server Groups on page 95 • Managing Guest Network Access on page 98 • Managing Users and Passwords on page 100 The wireless controller follows a configuration template called profile groups. Each access point at any instance operates using one profile group. A profile group includes all types of configuration that can be configured uniquely per access point, including 8 SSIDs per radio. The basic configuration menu selections cater to simple networks. In these screens, configuration applies to all the access points by default. There is no concept of different profile groups. The advanced menu selections cater to large and complex networks. Here you can create separate policies per profile group such as the wireless-on/off schedule for access points, channel allocation schedule. The SSIDs can be different per profile group. This allows the administrator of a complex network to fine-tune the configuration to meet requirements. It is important to know how to configure your network and decide which model fits better for your needs, basic or advanced. Once you follow one, it is easy to the use the same for all configuration pages. Managing Wireless Security Profiles Profiles are sets of configuration that can be applied to an access point. The configuration includes radio parameters, load balancing, and rate limit parameters. Each access point in managed mode is capable of supporting 8 profiles per radio. This means that the dual radio WNDAP350 access point can support 16 profiles in total. Setting up profiles allows you to configure the WLAN network offline. Then, when the WLAN network is up and running, you can push the configuration onto managed access points. You can configure profiles and profile groups without worrying about the state of the access Chapter 8: Configuring Security and Wireless Security Profiles | 83