Netgear WC7520 WC7520 Reference Manual - Page 87
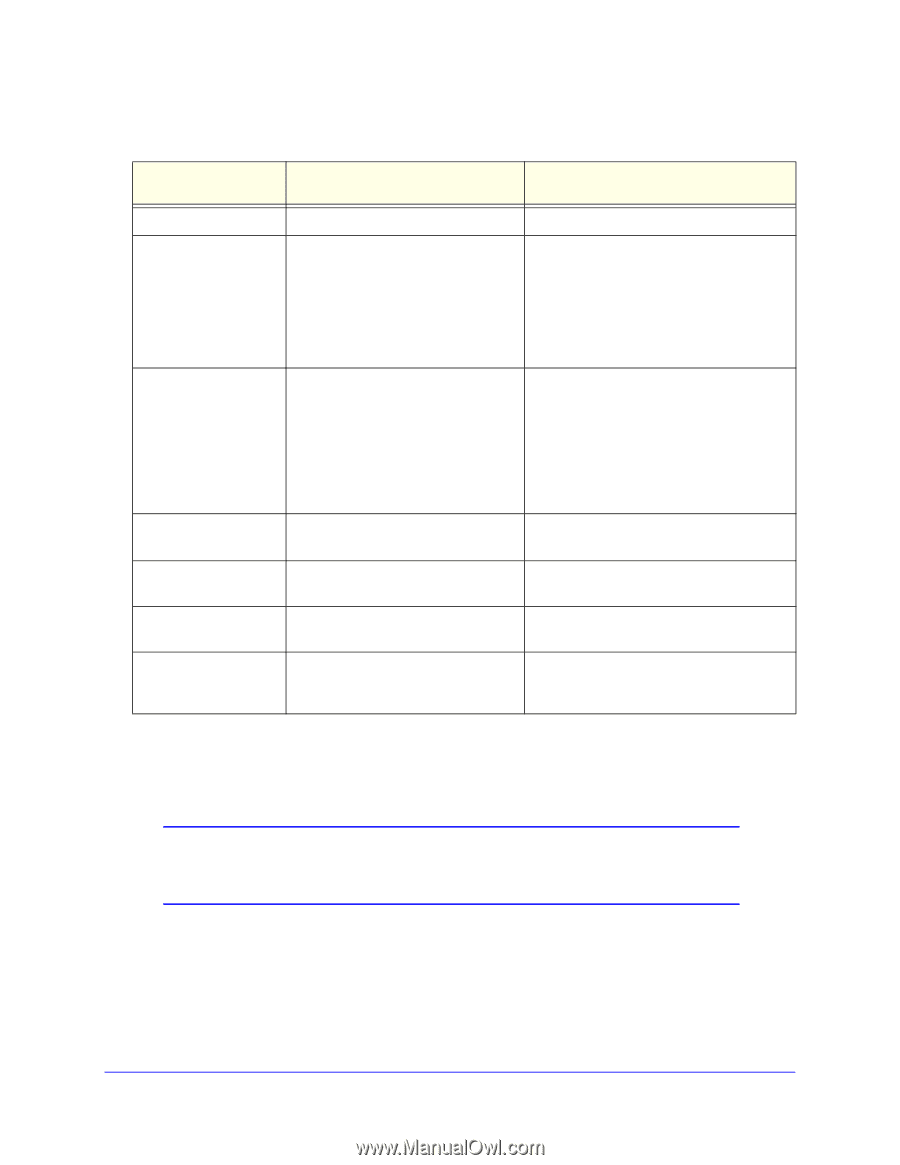
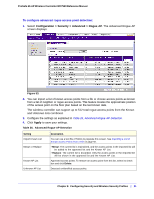
Configuring Advanced Security Profiles for Access Point Groups, Table 23.
 |
UPC - 606449072969
View all Netgear WC7520 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 87 highlights
ProSafe 20-AP Wireless Controller WC7520 Reference Manual Table 23. Network Authentication and Data Encryption Network Authentication Open Shared Key Legacy 802.1x WPA with RADIUS WPA2 with RADIUS WPA-PSK WPA2-PSK WPA2-PSK WPA and WPA2 WPA-PSK/WPA2-PSK Data Encryption Description None. No encryption. WEP. • 64-bit WEP encryption uses 40/64 bit encryption. • 128-bit WEP encryption uses 104/128 bit encryption. • 152-bit WEP is a proprietary mode that works only with other wireless devices that support this mode. • Select the WPA2 option only if all clients support WPA2. If this option is selected, you must use AES. • WPA/WPA2 with RADIUS allows clients to use either WPA (with TKIP) or WPA2 (with AES). If this option is selected, you must use TKIP + AES encryption. All require RADIUS configuration. TKIP or TKIP + AES and a WPA passphrase (network key). Standard encryption method for WPA2. AES and TKIP + AES . Some clients support AES with WPA, but this is not supported by this access point. TKIP + AES encryption and enter the Clients can use either WPA (with TKIP) or WPA passphrase (network key). WPA2 (with AES). TKIP + AES. Broadcast packets use TKIP. For unicast (point-to-point) transmissions, WPA clients use TKIP, and WPA2 clients use AES. Configuring Advanced Security Profiles for Access Point Groups Note: Not all networks require access point groups. See Chapter 6, Managing Access Point Groups for more information about access point groups. The Profile Groups screen lets you edit up to eight security profiles for managed access points in the selected group. The number of security profiles applied to managed access point depends on the supported profiles per access point. Separate profiles are applied to 802.11b/bg/ng and 802.11a/na mode radios. Chapter 8: Configuring Security and Wireless Security Profiles | 87