D-Link DGS-3324SR Product Manual - Page 180
OSPF Authentication, Message Digest Authentication (MD-5), Simple Password Authentication
 |
UPC - 790069262067
View all D-Link DGS-3324SR manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 180 highlights
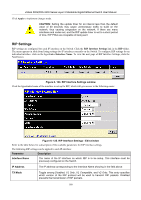
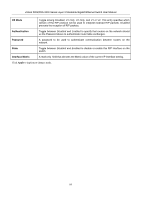
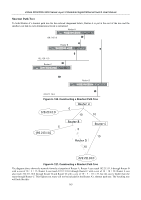
xStack DGS/DXS-3300 Series Layer 3 Stackable Gigabit Ethernet Switch User Manual Router link-state updates are flooded to all routers in the current area. These updates describe the destinations reachable through all of the router's interfaces. Summary link-state updates are generated by Border Routers to distribute routing information about other networks within the AS. Normally, all Summary link-state updates are forwarded to the backbone (area 0) and are then forwarded to all other areas in the network. Border Routers also have the responsibility of distributing routing information from the Autonomous System Border Router in order for routers in the network to get and maintain routes to other Autonomous Systems. Network link-state updates are generated by a router elected as the Designated Router on a multi-access segment (with more than one attached router). These updates describe all of the routers on the segment and their network connections. External link-state updates carry routing information to networks outside the Autonomous System. The Autonomous System Border Router is responsible for generating and distributing these updates. OSPF Authentication OSPF packets can be authenticated as coming from trusted routers by the use of predefined passwords. The default for routers is to use not authentication. There are two other authentication methods − simple password authentication (key) and Message Digest authentication (MD-5). Message Digest Authentication (MD-5) MD-5 authentication is a cryptographic method. A key and a key-ID are configured on each router. The router then uses an algorithm to generate a mathematical "message digest" that is derived from the OSPF packet, the key and the key-ID. This message digest (a number) is then appended to the packet. The key is not exchanged over the wire and a non-decreasing sequence number is included to prevent replay attacks. Simple Password Authentication A password (or key) can be configured on a per-area basis. Routers in the same area that participate in the routing domain must be configured with the same key. This method is possibly vulnerable to passive attacks where a link analyzer is used to obtain the password. Backbone and Area 0 OSPF limits the number of link-state updates required between routers by defining areas within which a given router operates. When more than one area is configured, one area is designated as area 0 − also called the backbone. The backbone is at the center of all other areas − all areas of the network have a physical (or virtual) connection to the backbone through a router. OSPF allows routing information to be distributed by forwarding it into area 0, from which the information can be forwarded to all other areas (and all other routers) on the network. In situations where an area is required, but is not possible to provide a physical connection to the backbone, a virtual link can be configured. Virtual Links Virtual links accomplish two purposes: • Linking an area that does not have a physical connection to the backbone. • Patching the backbone in case there is a discontinuity in area 0. Areas Not Physically Connected to Area 0 All areas of an OSPF network should have a physical connection to the backbone, but is some cases it is not possible to physically connect a remote area to the backbone. In these cases, a virtual link is configured to connect the remote area to the backbone. A virtual path is a logical path between two border routers that have a common area, with one border router connected to the backbone. 165