HP BladeSystem bc2800 Embedded Web System User Guide for the HP BladeSystem PC - Page 30
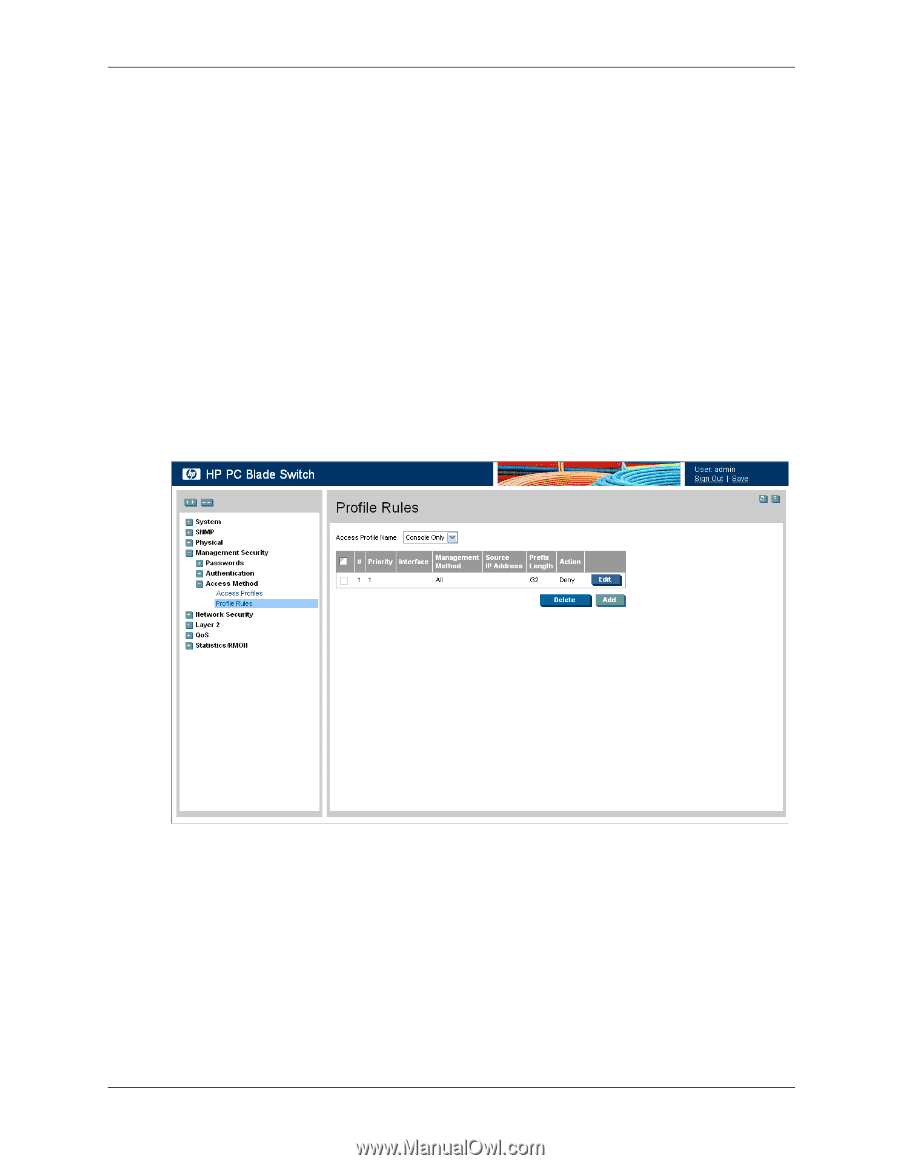
Defining Profile Rules
 |
View all HP BladeSystem bc2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 30 highlights
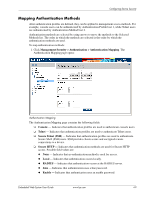
Configuring Device Security Defining Profile Rules Access profiles can contain up to 128 rules that determine which users can manage the switch module, and by which methods. Users can also be blocked from accessing the device. Rules are composed of filters including: ■ Rule Priority ■ Interface ■ Management Method ■ IP Address ■ Prefix Length ■ Forwarding Action The rule order is essential as packets are matched on a first-fit basis. To define profile rules: 1. Click Management Security > Access Method > Profile Rules. The Profile Rules page opens: Profile Rules The Profile Rules page contains the following fields: ❏ Access Profile Name - Displays the access profile to which the rule is attached. ❏ Priority - Defines the rule priority. When the packet is matched to a rule, user groups are either granted or denied device management access. The rule number is essential to matching packets to rules, as packets are matched on a first-fit basis. ❏ Interface - Indicates the interface type to which the rule applies. The possible field values are: ◆ Port - Attaches the rule to the selected port. ◆ LAG - Attaches the rule to the selected LAG. 4-4 www.hp.com Embedded Web System User Guide