HP BladeSystem bc2800 Embedded Web System User Guide for the HP BladeSystem PC - Page 31
Access Profile Name, Priority
 |
View all HP BladeSystem bc2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
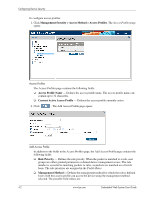
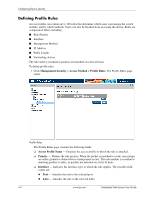
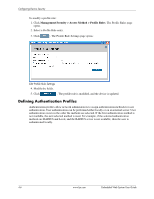
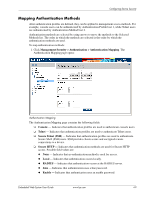
Configuring Device Security ◆ VLAN - Attaches the rule to the selected VLAN. ❏ Management Method - Defines the management method for which the rule is defined. Users with this access profile can access the device using the management method selected. The possible field values are: ◆ All - Assigns all management methods to the rule. ◆ Telnet - Assigns Telnet access to the rule. If selected, users accessing the device using Telnet, meeting access profile criteria, are permitted or denied access to the device. ◆ Secure Telnet (SSH) - Assigns SSH access to the rule. If selected, users accessing the device using Telnet, meeting access profile criteria, are permitted or denied access to the device. ◆ HTTP - Assigns HTTP access to the rule. If selected, users accessing the device using HTTP, meeting access profile criteria, are permitted or denied access to the device. ◆ Secure HTTP (HTTPS) - Assigns HTTPS access to the rule. If selected, users accessing the device using HTTPS, meeting access profile criteria, are permitted or denied access to the device. ◆ SNMP - Assigns SNMP access to the rule. If selected, users accessing the device using SNMP, meeting access profile criteria, are permitted or denied access to the device. ❏ Source IP Address - Defines the interface source IP address to which the rule applies. ❏ Prefix Length - Defines the number of bits that comprise the source IP address prefix, or the network mask of the source IP address. ❏ Action -Defines the action attached to the rule. The possible field values are: ◆ Permit - Permits access to the device. ◆ Deny - Denies access to the device. This is the default. 2. Click . Add Profile Rule 3. Define the Access Profile Name, Priority, Management Method, Interface, Source IP Address, Network Mask or Prefix Length, and Action fields. 4. Click updated. . The profile rule is added to the access profile, and the device is Embedded Web System User Guide www.hp.com 4-5