HP BladeSystem bc2800 Embedded Web System User Guide for the HP BladeSystem PC - Page 33
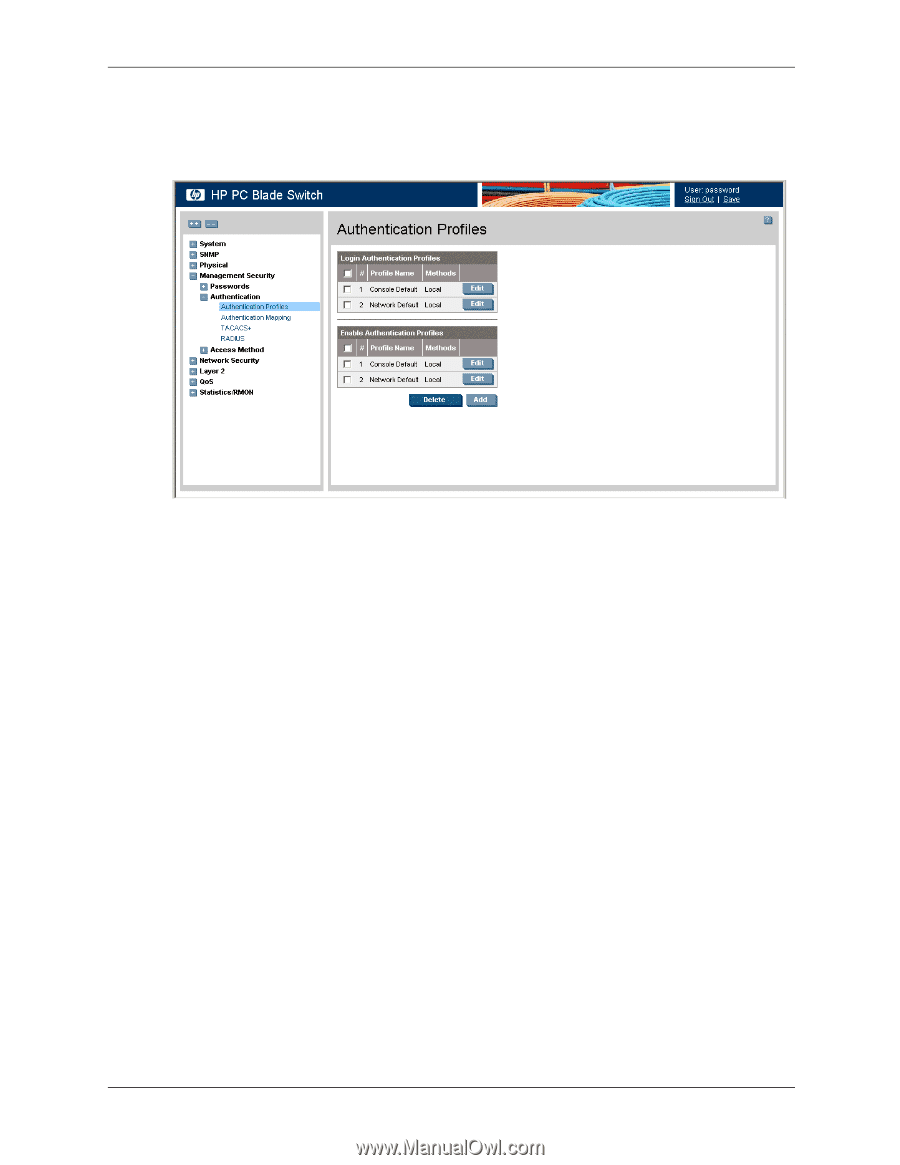
Management, Security > Authentication > Authentication Profiles, Profile Name, Methods, Local
 |
View all HP BladeSystem bc2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 33 highlights
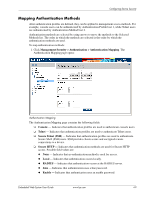
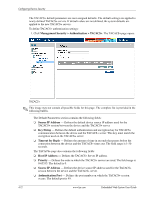
Configuring Device Security To define authentication profiles: 1. Click Management Security > Authentication > Authentication Profiles. The Authentication Profiles page opens. : Authentication Profiles The Authentication Profiles page contains the following sections: ❏ The Login Authentication Profiles section allows network administrators to select the authentication method by which system users are logged onto the device. ❏ The Enable Authentication Profiles section allows network administrators to select the method by which users are enabled on the system. Each section on the Authentication Profiles page contains the following fields: ❏ Profile Name - Contains a list of user-defined authentication profile lists to which user-defined authentication profiles are added. ❏ Methods - Defines the user authentication methods. The possible field values are: ◆ None - Assigns no authentication method to the authentication profile. ◆ Local - Authenticates the user at the device level. The device checks the user name and password for authentication. ◆ RADIUS - Authenticates the user at the RADIUS server. For more information, see "Defining RADIUS Settings." ◆ TACACS+ - Authenticates the user at the TACACS+ server. For more information, see "Defining TACACS+ Authentication." ◆ Line - Authenticates the user using a line password. ◆ Enable - Authenticates the user using an enable password. Embedded Web System User Guide www.hp.com 4-7