HP BladeSystem bc2800 Embedded Web System User Guide for the HP BladeSystem PC - Page 57
Configuring Traffic Control
 |
View all HP BladeSystem bc2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 57 highlights
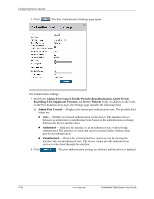
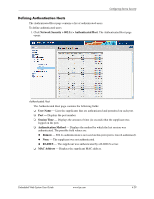
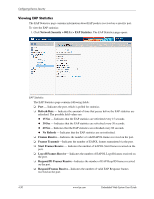
Configuring Device Security ❏ Request ID Frames Transmit-Indicates the number of EAP Req/ID frames transmitted via the port. ❏ Request Frames Transmit-Indicates the number of EAP Request frames transmitted via the port. ❏ Invalid Frames Receive-Indicates the number of unrecognized EAPOL frames received on this port. ❏ Length Error Frames Receive-Indicates the number of EAPOL frames with an invalid Packet Body Length received on this port. ❏ Last Frame Version-Indicates the protocol version number attached to the most recently received EAPOL frame. ❏ Last Frame Source-Indicates the source MAC address attached to the most recently received EAPOL frame. Configuring Traffic Control This section contains information for managing both port security and storm control, and includes the following topics: ■ Defining Access Control Lists ■ Managing Port Security ■ Enabling Storm Control Defining Access Control Lists Access Control Lists (ACL) allow network managers to define classification actions and rules for specific ingress ports. Packets entering an ingress port, with an active ACL, are either admitted or denied entry and the ingress port is disabled. If they are denied entry, the user can disable the port. For example, an ACL rule is defined that states that port number 20 can receive TCP packets, however, if a UDP packet is received, the packet is dropped. ACLs are composed of Access Control Entries (ACEs) that are made of the filters that determine traffic classifications. The total number of ACEs that can be defined in all ACLs together is 1024. The following filters can be defined as ACEs: ■ Source Port IP Address and Wildcard Mask - Filters the packets by the Source port IP address and wildcard mask. ■ Destination Port IP Address and Wildcard Mask - Filters the packets by the Destination port IP address and wildcard mask. ■ ACE Priority - Filters the packets by the ACE priority. ■ Protocol - Filters the packets by the IP protocol. ■ DSCP - Filters the packets by the DiffServ Code Point (DSCP) value. ■ IP Precedence - Filters the packets by the IP Precedence. ■ Action - Indicates the action assigned to the packet matching the ACL. Packets are forwarded or dropped. In addition, the port can be shut down, a trap can be sent to the network administrator, or the packet is assigned rate limiting restrictions for forwarding. This section contains the following topics: ■ Defining IP Based Access Control Lists Embedded Web System User Guide www.hp.com 4-31