HP BladeSystem bc2800 Embedded Web System User Guide for the HP BladeSystem PC - Page 35
Mapping Authentication Methods
 |
View all HP BladeSystem bc2800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 35 highlights
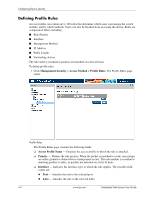
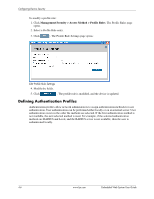
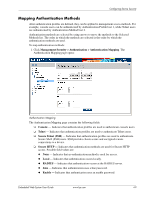
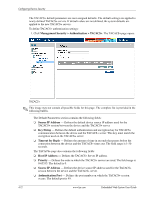
Configuring Device Security Mapping Authentication Methods After authentication profiles are defined, they can be applied to management access methods. For example, console users can be authenticated by Authentication Profile List 1, while Telnet users are authenticated by Authentication Method List 2. Authentication methods are selected by using arrows to move the methods to the Selected Methods list. The order in which the methods are selected is the order by which the authentication methods are used. To map authentication methods: 1. Click Management Security > Authentication > Authentication Mapping. The Authentication Mapping page opens: Authentication Mapping The Authentication Mapping page contains the following fields: ❏ Console - Indicates that authentication profiles are used to authenticate console users. ❏ Telnet - Indicates that authentication profiles are used to authenticate Telnet users. ❏ Secure Telnet (SSH) - Indicates that authentication profiles are used to authenticate Secure Shell (SSH) users. SSH provides clients secure and encrypted remote connections to a device. ❏ Secure HTTP - Indicates that authentication methods are used for Secure HTTP access. Possible field values are: ◆ None - Indicates that no authentication method is used for access. ◆ Local - Indicates that authentication occurs locally. ◆ RADIUS - Indicates that authentication occurs at the RADIUS server. ◆ Line - Indicates that authentication uses a line password. ◆ Enable - Indicates that authentication uses an enable password. Embedded Web System User Guide www.hp.com 4-9