HP 6125XLG R2306-HP 6125XLG Blade Switch Fundamentals Configuration Guide - Page 38
Logging in through SSH, Configuring SSH login on the device
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
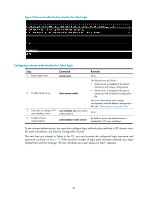
Logging in through SSH SSH offers a secure method for remote login. By providing encryption and strong authentication, it protects devices against attacks such as IP spoofing and plain text password interception. For more information, see Security Configuration Guide. You can use an SSH client to log in to the device for remote management, or use the device as an SSH client to log in to an SSH server. By default, SSH login is disabled on the device. To log in to the device through SSH, you must log in to the device through the console or AUX port and configure SSH login on the device first. Configuring SSH login on the device This section provides the configuration procedure for when the SSH client authentication method is password. For more information about SSH and publickey authentication configuration, see Security Configuration Guide. To configure SSH login on the device: Step 1. Enter system view. 2. Create local key pairs. 3. Enable SSH server. 4. Create an SSH user and specify the authentication mode. 5. Enter one or multiple VTY user interface views. 6. Enable scheme authentication. Command system-view public-key local create { dsa | rsa | ecdsa } [name key-name ] ssh server enable • In non-FIP mode: ssh user username service-type stelnet authentication-type { password | { any | password-publickey | publickey } assign publickey keyname } • In FIP mode: ssh user username service-type stelnet authentication-type { password | password-publickey assign publickey keyname } user-interface vty first-number [ last-number ] authentication-mode scheme Remarks N/A By default, no local key pairs are created. By default, SSH server is disabled. By default, no SSH user is configured on the device. N/A In non-FIPS mode, password authentication is enabled for VTY user interfaces by default. In FIPS mode, scheme authentication is enabled for VTY user interfaces by default. 31