HP 6125XLG R2306-HP 6125XLG Blade Switch Fundamentals Configuration Guide - Page 55
Changing the VLAN policy of a user role, Changing the VPN instance policy of a user role, Assigning
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 55 highlights
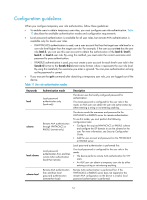
Changing the VLAN policy of a user role Step 1. Enter system view. 2. Enter user role view. Command system-view role name role-name 3. Enter user role VLAN policy view. vlan policy deny 4. (Optional.) Specify a list of VLANs accessible to the permit vlan vlan-id-list user role. Remarks N/A N/A By default, the VLAN policies of user roles permit access to all VLANs. This command disables the access of the user role to any VLAN. By default, no accessible VLANs are configured. To add more accessible VLANs, repeat this step. Changing the VPN instance policy of a user role Step 1. Enter system view. 2. Enter user role view. 3. Enter user role VPN instance policy view. Command system-view role name role-name vpn-instance policy deny 4. (Optional.) Specify a list of VPNs accessible to the user permit vpn-instance role. vpn-instance-name& Remarks N/A N/A By default, the VPN policies of user roles permit access to all VPNs. This command disables the access of the user role to any VPN. By default, no accessible VPNs are configured. To add more accessible VPNs, repeat this step. Assigning user roles To control user access to the system, you must assign at least one user role. Make sure at least one user role among the user roles assigned by the server exists on the device. User role assignment procedure varies with remote AAA authentication users, local AAA authentication users, and non-AAA authentication users (see "Assigning user roles"). For more information about AAA authentication, see Security Configuration Guide. Enabling the default user role function An AAA authentication user must have at least one user role to log in to the device. The default user role function assigns the network-operator user role to a local or remote AAA authenticated user if the AAA server has not authorized the user to use any user roles. Without the function, AAA authenticated users cannot access the system if they have no user role authorization. To enable the default user role function for AAA authentication users: 48