HP 6125XLG R2306-HP 6125XLG Blade Switch Fundamentals Configuration Guide - Page 60
RBAC configuration examples, RBAC configuration example for local AAA authentication users
 |
View all HP 6125XLG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 60 highlights
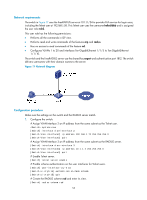
RBAC configuration examples RBAC configuration example for local AAA authentication users Unless otherwise noted, devices in the configuration example are operating in non-FIPS mode. Network requirements The switch in Figure 16 performs local AAA authentication for the Telnet user at 192.168.1.58. This Telnet user has the username user1@bbb and is assigned the user role role1. Configure role1 to have the following permissions: • Executes the read commands of any feature. • Configures no VLANs except VLANs 10 to 20. Figure 16 Network diagram Configuration procedure # Assign an IP address to VLAN-interface 2, the interface connected to the Telnet user. system-view [Switch] interface vlan-interface 2 [Switch-Vlan-interface2] ip address 192.168.1.70 255.255.255.0 [Switch-Vlan-interface2] quit # Enable Telnet server. [Switch] telnet server enable # Enable scheme authentication on the user interfaces for Telnet users. [Switch] user-interface vty 0 15 [Switch-ui-vty0-15] authentication-mode scheme [Switch-ui-vty0-15] quit # Enable local authentication and authorization for the ISP domain bbb. [Switch] domain bbb [Switch-isp-bbb] authentication login local [Switch-isp-bbb] authorization login local [Switch-isp-bbb] quit # Create the user role role1. [Switch] role name role1 # Configure rule 1 to permit the user role to access read commands of all features. [Switch-role-role1] rule 1 permit read feature # Configure rule 2 to permit the user role to create VLANs and access commands in VLAN view. [Switch-role-role1] rule 2 permit command system-view ; vlan * 53